NIS vs NIS2 Directive: Every Key Difference Listed
Key Takeaways on NIS vs NIS2 DifferencesNIS2 significantly ...

Author:
Tomislav Horvat

NIS2 significantly expands the scope beyond NIS1 to cover both "essential" and "important" entities across multiple new sectors.
Executive accountability shifts cybersecurity responsibility to the boardroom, with potential personal liability for management.
Organizations face a structured incident reporting timeline with strict deadlines: 24-hour initial notification, 72-hour follow-up, and one-month final report.
Security requirements now include seven mandatory elements including incident response, business continuity, and supply chain security.
Penalties increase dramatically under NIS2—up to €10M/2% of turnover for essential entities and €7M/1.4% for important entities.
EU-wide coordination improves through EU-CyCLONe and enhanced ENISA responsibilities for managing large-scale incidents.
Member States must transpose NIS2 by October 17, 2024, with complete entity identification required by April 17, 2025.
Organizations should start compliance preparation immediately given the comprehensive nature of the new requirements.

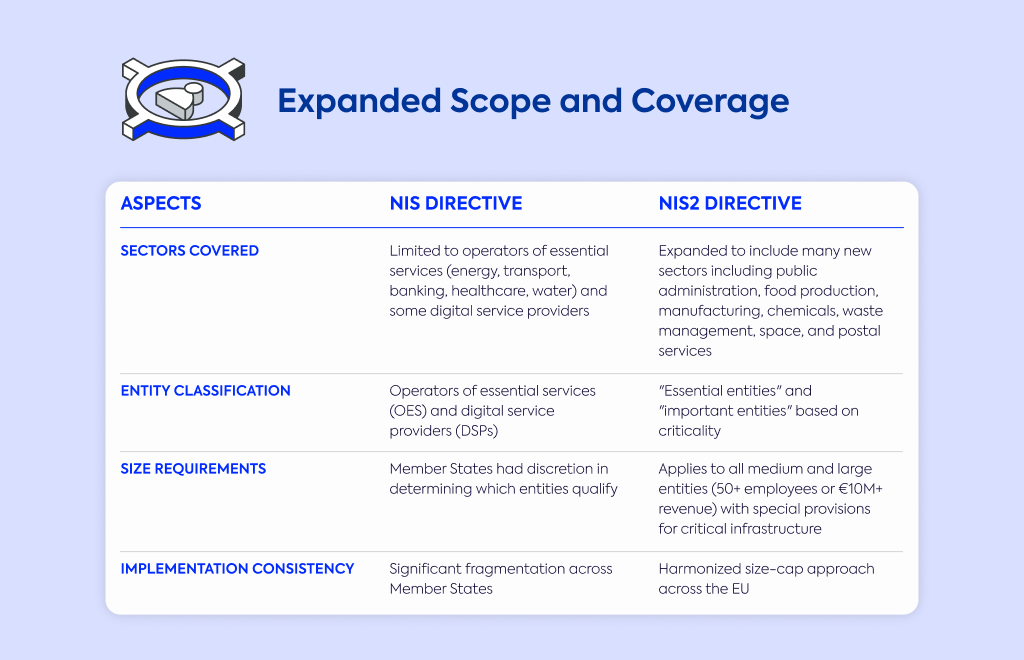
Aspect | NIS Directive | NIS2 Directive |
Sectors covered | Limited to operators of essential services (energy, transport, banking, healthcare, water) and some digital service providers | Expanded to include many new sectors including public administration, food production, manufacturing, chemicals, waste management, space, and postal services |
Entity classification | Operators of essential services (OES) and digital service providers (DSPs) | "Essential entities" and "important entities" based on criticality |
Size requirements | Member States had discretion in determining which entities qualify | Applies to all medium and large entities (50+ employees or €10M+ revenue) with special provisions for critical infrastructure |
Implementation consistency | Significant fragmentation across Member States | Harmonized size-cap approach across the EU |
The original NIS Directive had a relatively narrow focus, primarily covering operators of essential services (OES) in sectors like energy, transport, banking, healthcare, and water.
It also included digital service providers (DSPs), but these were limited to just online marketplaces, search engines, and cloud services.
NIS2 dramatically expands this scope.
The updated directive now distinguishes between "essential entities" and "important entities" based on how critical they are to society and the economy.
You'll find many new sectors added under NIS2 protection, including public administration, food production, manufacturing, chemicals, waste management, space, and postal services.
One of the most significant changes affects which organizations must comply.
NIS2 applies to all medium-sized and large entities with over 50 employees or annual revenue exceeding €10 million in covered sectors.
Special provisions exist for entities deemed critical infrastructure regardless of size, ensuring no important service provider falls through the cracks.
The first NIS implementation led to serious fragmentation across Europe.
Some countries identified numerous essential service operators while others recognized very few, creating security gaps and inconsistent protection.
NIS2 fixes this problem by removing Member States' discretion in determining which entities qualify as essential and implementing a standardized size-cap approach across the EU.
Aspect | NIS Directive | NIS2 Directive |
Executive accountability | Limited management accountability with vague responsibility structure | Explicit management responsibility with potential personal liability |
Training requirements | No specific management training requirements | Regular cybersecurity training required for management teams |
Cybersecurity positioning | Often treated as an IT department responsibility | Integrated into core corporate governance |
Role definition | Limited guidance on cybersecurity roles | Clear definition of roles and responsibilities required at all levels |
NIS2 makes executive management directly responsible for cybersecurity compliance, moving away from NIS1's vaguer accountability structure.
This change puts cybersecurity firmly in the boardroom instead of leaving it solely to IT departments.
Under the new directive, senior management must approve cybersecurity risk assessment measures and oversee their implementation.
You need to ensure your organization's executives receive regular cybersecurity training so they can provide proper oversight.
This isn't optional—management can actually be held personally liable for non-compliance with NIS2 provisions.
Organizations must clearly define cybersecurity roles and responsibilities at all levels.
This structured approach integrates cybersecurity into core corporate governance rather than treating it as a technical afterthought, creating a more robust security culture throughout your organization.

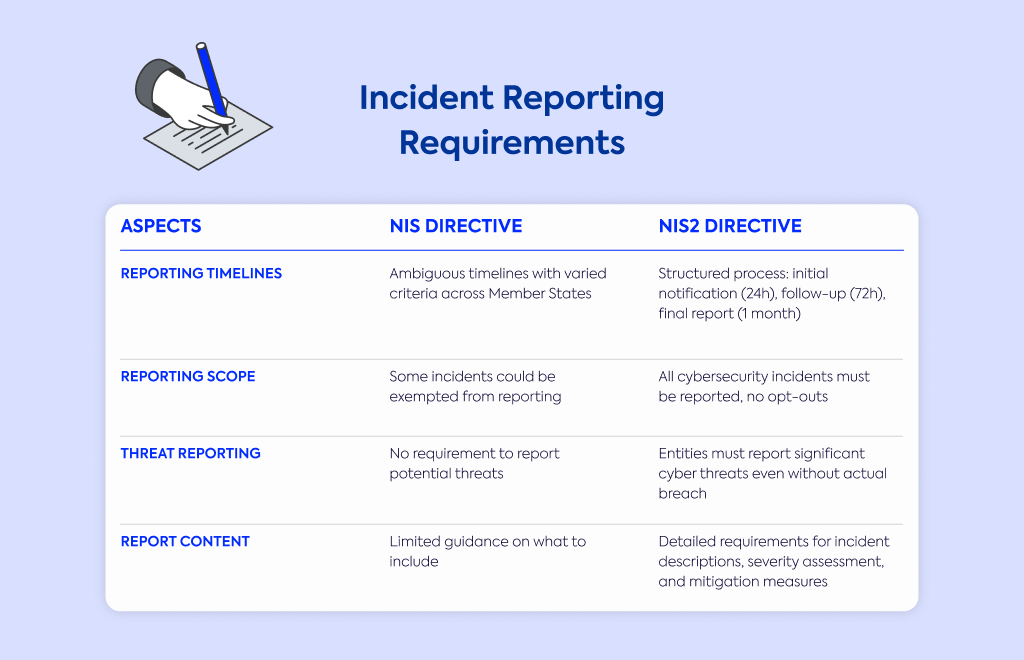
Aspect | NIS Directive | NIS2 Directive |
Reporting timelines | Ambiguous timelines with varied criteria across Member States | Structured process: initial notification (24h), follow-up (72h), final report (1 month) |
Reporting scope | Some incidents could be exempted from reporting | All cybersecurity incidents must be reported, no opt-outs |
Threat reporting | No requirement to report potential threats | Entities must report significant cyber threats even without actual breach |
Report content | Limited guidance on what to include | Detailed requirements for incident descriptions, severity assessment, and mitigation measures |
The original NIS Directive left too much room for interpretation when it came to reporting incidents.
Timelines were ambiguous and criteria varied widely across Member States. NIS2 fixes this with a structured, multi-stage reporting process that leaves no room for doubt.
When an incident occurs, you now have specific deadlines to meet: initial notification within 24 hours, a follow-up report within 72 hours, and a final detailed report within one month.
Your initial report must indicate whether the incident resulted from malicious action, while the final report needs to include a comprehensive incident description, severity assessment, impact analysis, threat identification, and details about applied mitigation measures.
All cybersecurity incidents must be reported under NIS2, eliminating the opt-out opportunities that existed previously.
The directive also introduces a new requirement to report significant cyber threats that could potentially result in incidents, even if no breach has actually occurred.
For organizations outside the NIS2 scope, voluntary reporting is encouraged without subjecting you to additional obligations.
This creates a safer information-sharing environment that benefits the entire cybersecurity ecosystem.
Aspect | NIS Directive | NIS2 Directive |
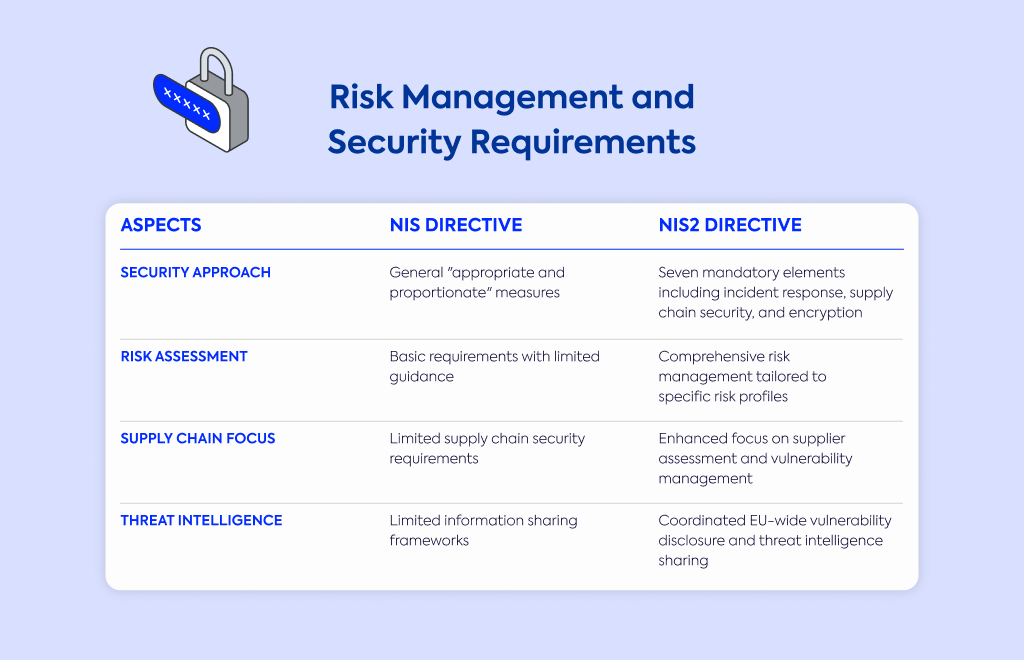
Security approach | General "appropriate and proportionate" measures | Seven mandatory elements including incident response, supply chain security, and encryption |
Risk assessment | Basic requirements with limited guidance | Comprehensive risk management tailored to specific risk profiles |
Supply chain focus | Limited supply chain security requirements | Enhanced focus on supplier assessment and vulnerability management |
Threat intelligence | Limited information sharing frameworks | Coordinated EU-wide vulnerability disclosure and threat intelligence sharing |
NIS2 takes a more sophisticated approach to security requirements than its predecessor.
Instead of general security measures, the updated directive mandates comprehensive risk management tailored to each organization's specific risk profile.
Every company must implement seven key elements: incident response, business continuity, supply chain security, network security, access controls, vulnerability management, and encryption.
Your security controls need to be proportionate to the actual risks your organization faces, creating a more efficient and effective protection strategy.
Supply chain security receives special attention in NIS2.
You must assess your suppliers' security practices and identify potential vulnerabilities that could impact your operations.
The directive also introduces coordinated EU-wide vulnerability disclosure and threat intelligence sharing frameworks to help organizations stay ahead of emerging threats.
Your technical and organizational measures must prevent incidents while limiting their impact on service delivery when they do occur.
This comprehensive approach addresses both technical and non-technical factors, including potential state interference with suppliers - a concern that wasn't explicitly covered under the original directive.
Aspect | NIS Directive | NIS2 Directive |
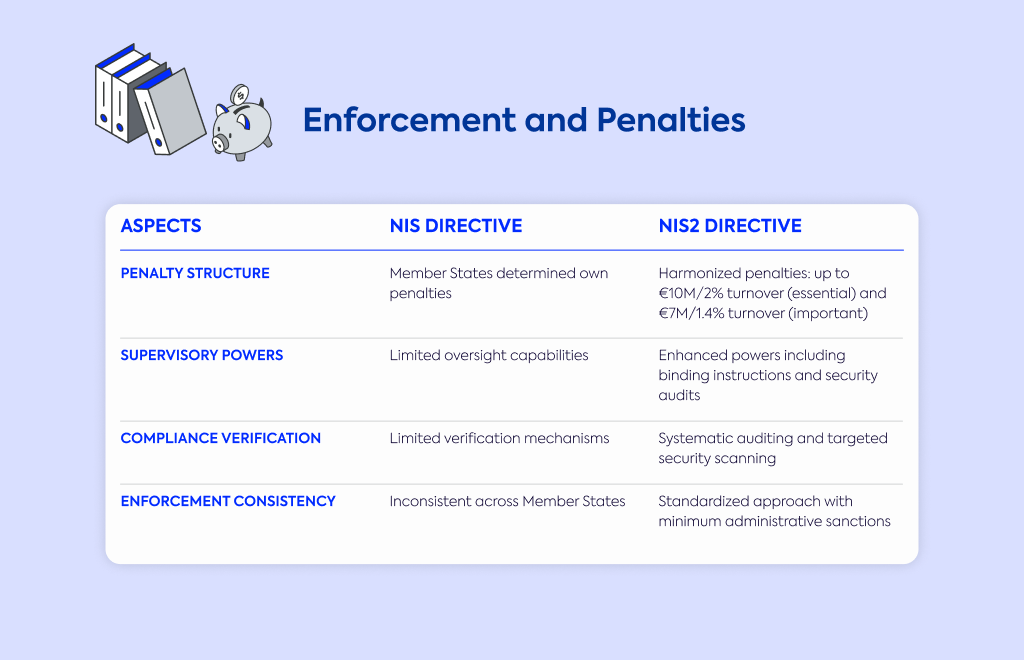
Penalty structure | Member States determined own penalties | Harmonized penalties: up to €10M/2% turnover (essential) and €7M/1.4% turnover (important) |
Supervisory powers | Limited oversight capabilities | Enhanced powers including binding instructions and security audits |
Compliance verification | Limited verification mechanisms | Systematic auditing and targeted security scanning |
Enforcement consistency | Inconsistent across Member States | Standardized approach with minimum administrative sanctions |
The enforcement landscape changes dramatically under NIS2.
The original directive allowed Member States to determine their own penalties, resulting in inconsistent enforcement across Europe.
NIS2 establishes harmonized, stricter enforcement mechanisms and a minimum list of administrative sanctions that apply everywhere.
Financial penalties become much more severe: essential entities face fines up to €10 million or 2% of global annual turnover, while important entities may incur penalties up to €7 million or 1.4% of global annual turnover.
These numbers should grab your attention if you're responsible for compliance budgets.
Supervisory bodies receive enhanced powers under NIS2, including the ability to issue binding instructions and conduct security audits.
National authorities can subject non-compliant organizations to enhanced supervision or monitoring and may require you to remedy identified security deficiencies within specific timeframes.
The directive includes provisions for systematic auditing and targeted security scanning to verify compliance, making it much harder to fly under the radar with inadequate security practices.
Aspect | NIS Directive | NIS2 Directive |
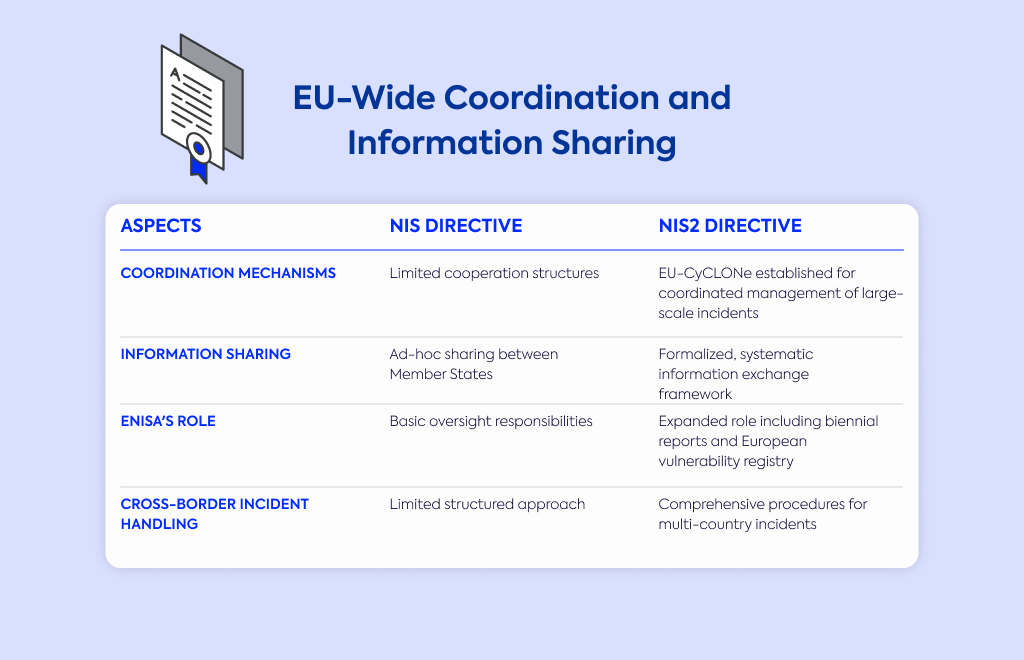
Coordination mechanisms | Limited cooperation structures | EU-CyCLONe established for coordinated management of large-scale incidents |
Information sharing | Ad-hoc sharing between Member States | Formalized, systematic information exchange framework |
ENISA's role | Basic oversight responsibilities | Expanded role including biennial reports and European vulnerability registry |
Cross-border incident handling | Limited structured approach | Comprehensive procedures for multi-country incidents |
NIS2 creates stronger coordination mechanisms across the European Union.
The directive establishes EU-CyCLONe (EU Cyber Crisis Liaison Organisation Network) to support coordinated management of large-scale cybersecurity incidents that affect multiple countries.
Information sharing between Member States becomes more formalized and systematic under NIS2.
The NIS Cooperation Group's role strengthens in coordinating implementation and facilitating strategic cooperation, ensuring more consistent protection across borders.
ENISA (the EU Agency for Cybersecurity) receives expanded responsibilities, including preparing biennial reports on EU cybersecurity and maintaining a European vulnerability registry.
The agency serves as a central knowledge hub for cybersecurity best practices and threat intelligence.
The directive mandates analysis and sharing of threat intelligence across sectors to improve collective response capabilities.
A voluntary peer-learning mechanism helps organizations share effective practices with others in their industry.
Cross-border cooperation strengthens through structured procedures for handling incidents that affect multiple countries simultaneously.
Aspect | NIS Directive | NIS2 Directive |
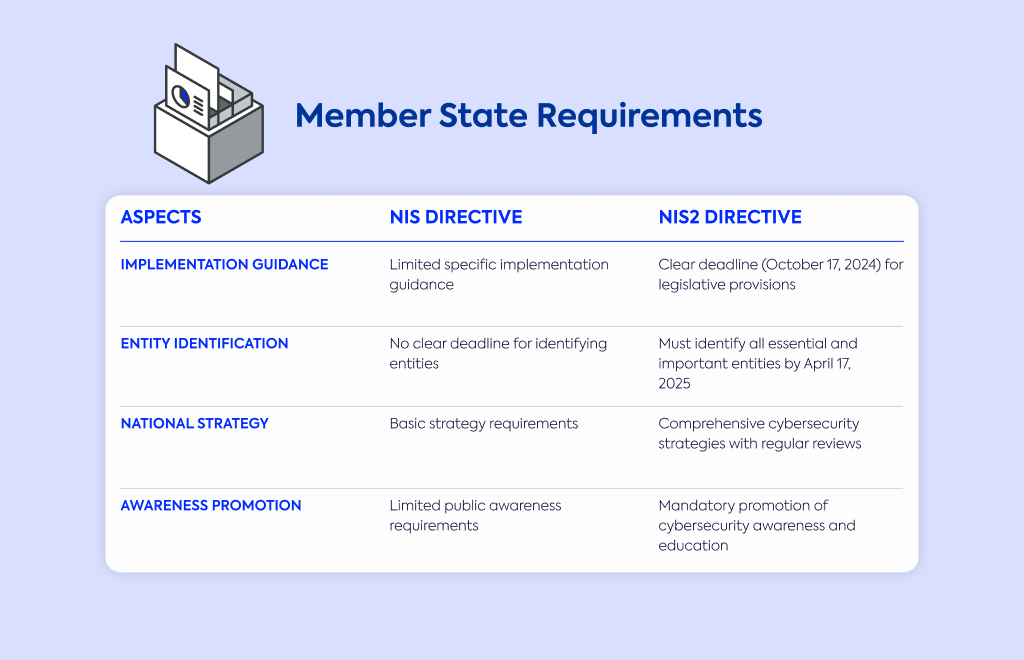
Implementation guidance | Limited specific implementation guidance | Clear deadline (October 17, 2024) for legislative provisions |
Entity identification | No clear deadline for identifying entities | Must identify all essential and important entities by April 17, 2025 |
National strategy | Basic strategy requirements | Comprehensive cybersecurity strategies with regular reviews |
Awareness promotion | Limited public awareness requirements | Mandatory promotion of cybersecurity awareness and education |
NIS2 imposes clearer obligations on Member States than the original directive did.
You'll see governments publishing necessary legislative provisions by October 17, 2024, whereas NIS1 provided less specific implementation guidance.
Each Member State must identify all essential and important entities within its borders by April 17, 2025.
They need to develop and implement comprehensive national cybersecurity strategies, regularly reviewing and updating them to address emerging threats.
Member States must establish well-resourced Computer Security Incident Response Teams (CSIRTs) with adequate training to handle security incidents effectively.
National Competent Authorities receive stronger supervisory and enforcement powers to ensure compliance with the directive's requirements.
Governments are required to promote cybersecurity awareness and education among citizens and businesses.
This broader approach recognizes that security culture needs to extend beyond regulated organizations to be truly effective.
Member States must periodically assess their cybersecurity frameworks and implement continuous improvement processes to keep pace with evolving threats.
Aspect | NIS Directive | NIS2 Directive |
Adoption date | July 2016 | November 28, 2022 |
Entry into force | May 2018 | January 16, 2023 |
Transposition deadline | Varied across Member States | October 17, 2024 (21 months from entry) |
Entity registration | No standardized registration process | Entities must register with relevant authorities in each operating country |
The Council of the European Union adopted NIS2 on November 28, 2022, and published it on December 27, 2022, officially replacing the original NIS Directive.
The new directive entered into force on January 16, 2023, starting the clock on implementation deadlines.
Member States have until October 17, 2024—21 months from entry into force—to transpose NIS2 into national law.
Organizations must register with relevant authorities in each EU country where they provide services, providing name, address, registration number, sector/subsector, contact details, and IP addresses.
All essential and important entities must be identified by April 17, 2025.
The transition from NIS1 to NIS2 maintains continuity while addressing the limitations identified in the original directive, giving organizations time to adapt to the new requirements.
If your organization falls under NIS2 scope, you should start preparing for compliance now.
The comprehensive nature of the new requirements means you'll likely need significant time to implement all necessary measures before the deadlines arrive.

The transition from NIS to NIS2 brings significant challenges for organizations across the EU.
With stricter requirements, expanded scope, and substantial penalties for non-compliance, navigating these changes requires specialized expertise.
At Gauss, we understand the complexities of NIS2 compliance and offer custom IT solutions to help your organization meet these new cybersecurity demands efficiently.
Our team of experts can guide you through the entire compliance process - from initial gap analysis to implementing the seven mandatory security elements and establishing proper incident reporting procedures.
Don't risk facing those €10 million penalties or damaging your organization's reputation.
Contact Gauss today to discuss how our tailored NIS2 compliance services can protect your business while turning regulatory requirements into opportunities for strengthening your overall security posture.