NIS vs NIS2 Directive: Every Key Difference Listed
Key Takeaways on NIS vs NIS2 DifferencesNIS2 significantly ...

Author:
Tomislav Horvat

Regular cybersecurity testing helps you find and fix vulnerabilities before attackers can exploit them
Combine multiple testing approaches—vulnerability scanning for quick automated checks and penetration testing to simulate real attacks
Balance technical testing with human-factor assessments since employees remain both your greatest vulnerability and strongest defense
Create clear testing scopes with SMART objectives, ensuring you test both external and internal systems
Follow security best practices like strong passwords, updated software, proper access controls, and regular backups to build a comprehensive security posture
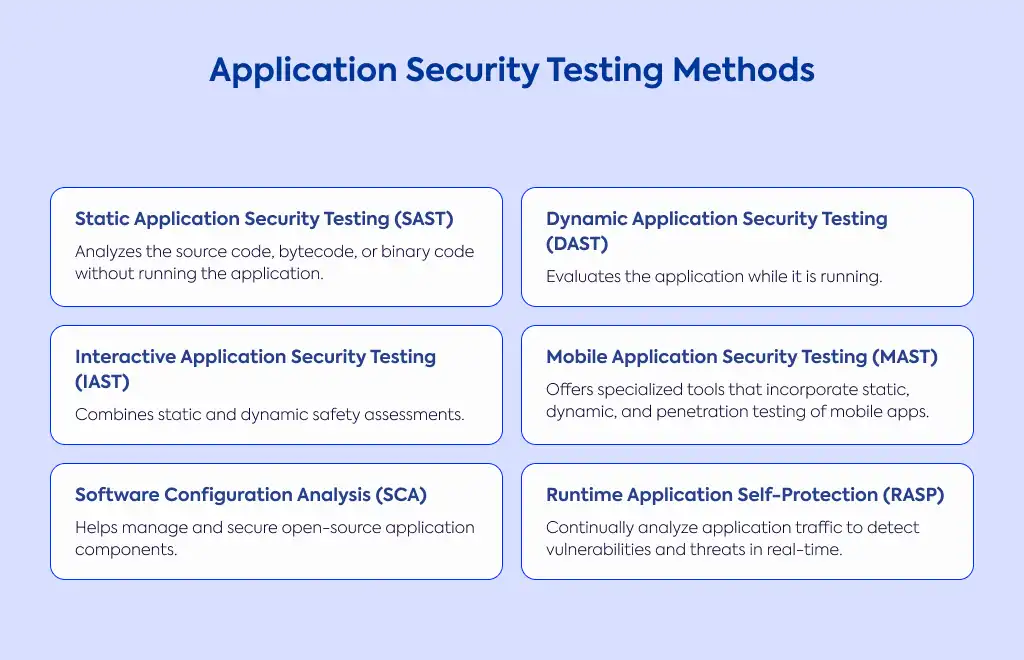
Have you ever wondered what keeps your digital information safe? At its core, cybersecurity testing helps identify potential vulnerabilities, misconfigurations, and weaknesses in software, computers, and networks. Think of it as a regular health check-up, but for your digital systems. When you test consistently, you can spot and fix security gaps before attackers have a chance to exploit them. Once issues are found, you're in a much better position to develop effective remediation strategies that reduce your overall exposure to cyber risks.
The digital world is constantly evolving, with attack surfaces expanding through cloud computing, Bring Your Own Device policies, and all those Internet of Things gadgets we've come to rely on. Good security testing ensures that your applications, networks, servers, and databases remain free of security flaws. You have options too—testing can be done manually by security professionals or through automated tools, depending on your specific needs.
What happens if you skip these important checks? Unfortunately, unaddressed vulnerabilities often lead to serious consequences, including loss of valuable information, revenue drops, reputation damage, and even customer exodus. It's like leaving your front door unlocked in a neighborhood known for break-ins—not the best strategy for protection.

Think of vulnerability scanning as your first line of defense—it's an automated assessment that searches for known and common vulnerabilities throughout your digital environment. These scanners work by gathering information about the applications running on your system and comparing them against databases of known vulnerable programs.
You can approach this in several ways: from outside your organization's network (external scanning), from within your network (internal scanning), without actively engaging with systems (non-intrusive or passive scanning), or by actively probing systems (intrusive scanning). What might these scans uncover? Common findings include missing security patches, weak passwords, malware infections, and various potential exposures.
Many organizations find that scheduling these scans according to their specific needs works best—perhaps weekly for critical systems, monthly for standard operations, or quarterly for less vulnerable assets. One of the great advantages of vulnerability scanning is how efficiently it handles large and complex applications, as it doesn't require access to source code. Consider this your essential first step in securing your network before implementing more advanced countermeasures.
Imagine hiring professional "burglars" who have your permission to try breaking into your systems—that's essentially what penetration testing does. These simulated cyberattacks help identify and exploit potential vulnerabilities in your organization. You might run these tests from outside your network to mimic external threats or from inside to simulate what might happen if someone within your organization went rogue.
What makes penetration testing particularly valuable is its ability to uncover hidden vulnerabilities that might otherwise go undetected, including zero-day threats (vulnerabilities unknown to software vendors) and business logic flaws. Unlike automated scans, trusted and certified security experts typically perform these tests manually, following a comprehensive process that includes defining the scope, gathering intelligence, analyzing vulnerabilities, modeling threats, attempting exploitation, collecting data, and providing detailed reports.
One of the key benefits of penetration testing is that it goes beyond simply identifying vulnerabilities—it helps determine the actual level of risk each vulnerability poses to your organization. This testing isn't just a good practice; it's often a requirement, such as for organizations that need to comply with the Payment Card Industry Data Security Standard (PCI-DSS).
When you undergo a security audit, you're essentially getting a comprehensive review of your organization's security policies, procedures, and controls against defined standards. It's like having an expert examine your entire security approach to ensure it aligns with industry standards or regulatory requirements, such as ISO 27001 or HIPAA.
These audits typically involve meticulous code review through line-by-line inspection and careful manual checking for security issues. In some cases, they might include techniques like fuzz testing, where random data is injected into your system to identify potential faults. Depending on your needs and resources, either independent contractors or internal staff can perform these audits.
Regular security audits help validate that your security policies and procedures are working as intended. When conducted on a consistent schedule, these audits make security flaws easier to spot and eliminate before they cause problems.
A good risk assessment helps you identify, analyze, and classify security risks facing your applications, software, or networks. Typically, these risks get categorized as Critical, High, Medium, or Low based on their potential impact and likelihood. From there, you can develop recommendations for mitigation measures and controls, prioritizing your response based on severity.
Many risk assessments use specialized techniques like threat modeling to evaluate how capable various threats are of exploiting weaknesses in your systems. The process typically follows four fundamental steps: identifying risks, analyzing them thoroughly, prioritizing them based on impact, and developing mitigation strategies.
How do you determine which risks need immediate attention? Generally, risks get prioritized based on two key factors: how likely they are to occur and the potential damage they could cause if they do happen. Since the risk landscape is constantly changing, it's important to perform these assessments regularly as new threats emerge, existing ones evolve, and others fade away. For consistency and thoroughness, many organizations align their assessment methodology with industry standards such as the OWASP Top 10 Risk Score.
Ethical hacking involves bringing in skilled security professionals to deliberately attempt to breach your system defenses—but in a controlled, authorized manner. Often referred to as white hat hacking, the primary goal is to expose flaws in your security rather than steal or compromise data.
This approach encompasses several specialized areas, including web application hacking, system hacking, web server hacking, and database hacking. When ethical hackers work, they typically employ three main types of scanning: port scanning to identify open communication channels, network scanning to map your system architecture, and vulnerability scanning to identify specific weaknesses.
What makes ethical hacking particularly valuable is its ability to find vulnerabilities that might remain hidden during more conventional testing methods. It provides a fresh perspective by examining systems before they go live and differs fundamentally from malicious hacking since no damage occurs during the process.
Think of a security posture assessment as a holistic health check for your organization's security infrastructure. It evaluates your overall security strength by analyzing defenses, vulnerabilities, policies, and controls all together. This gives you a comprehensive view of how well you're protected against cyber threats, identifying weaknesses and suggesting improvements.
Such assessments typically cover multiple areas, including network security, data protection practices, regulatory compliance, and incident response capabilities. Most organizations bring in external security or IT professionals to perform these assessments, with costs varying widely from hundreds to thousands of dollars depending on complexity and scope.
Consider this assessment as your first major step toward strengthening organizational security. The process usually follows a two-phase approach: first analyzing your current security controls, then conducting penetration testing to identify exploitable vulnerabilities. After completion, you'll receive a detailed report identifying weaknesses and proposing specific corrective measures.
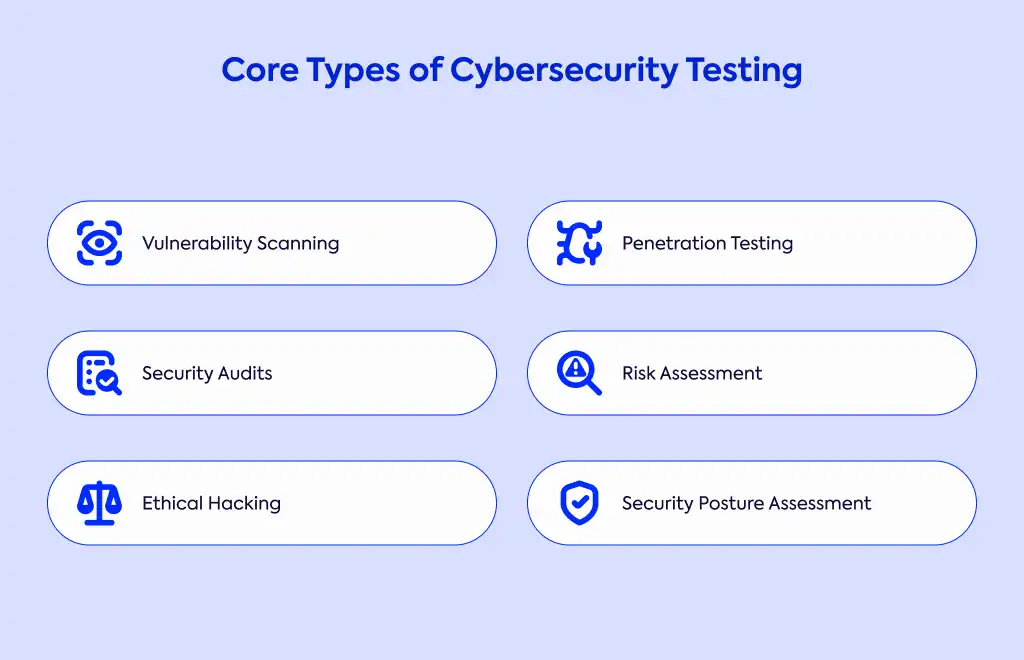
When it comes to securing applications, you have several testing methods at your disposal. Static Application Security Testing (SAST) analyzes your source code, bytecode, or binary code without actually running the application—think of it as examining the blueprint of a building. On the other hand, Dynamic Application Security Testing (DAST) evaluates your application while it's running, without needing to know about its internal code structure, similar to testing a building by trying different ways to enter it.
For a more comprehensive approach, Interactive Application Security Testing (IAST) combines both static and dynamic assessments. If you're developing mobile applications, Mobile Application Security Testing (MAST) offers specialized tools that incorporate static, dynamic, and penetration testing techniques designed specifically for mobile environments.
Other important methods include Software Configuration Analysis (SCA), which helps manage and secure open-source components in your applications, and Runtime Application Self-Protection (RASP), which continuously analyzes application traffic to detect vulnerabilities or external threats in real-time. Many organizations also benefit from secure code reviews, which involve line-by-line inspection of code to find security issues before software release.
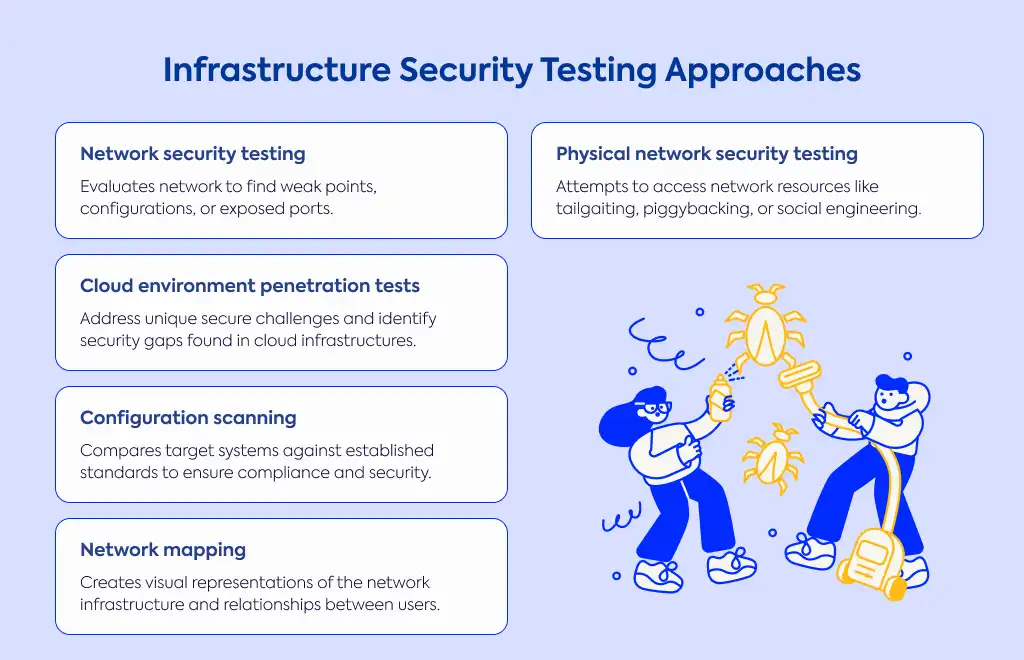
Protecting your infrastructure requires specialized testing approaches. Network security testing, for example, evaluates your networks by identifying weak points in access points, configurations, or exposed ports that could potentially be exploited.
If you're using cloud services, dedicated cloud environment penetration tests address the unique security challenges found in infrastructures like AWS, GCP, and Azure. Similarly, if you're working with containerized applications, Docker and Kubernetes penetration testing helps identify misconfigurations that could lead to security breaches.
Don't forget about wireless networks—specific tests can scan for security flaws like weak passwords or insecure protocols in your Wi-Fi setup. Configuration scanning compares your target systems against established standards from research organizations or regulatory bodies to ensure compliance and security.
Other valuable approaches include network mapping, which creates visual representations of your network infrastructure and relationships between users, and physical network security testing, which attempts to access network resources through methods like tailgating, piggybacking, or social engineering.
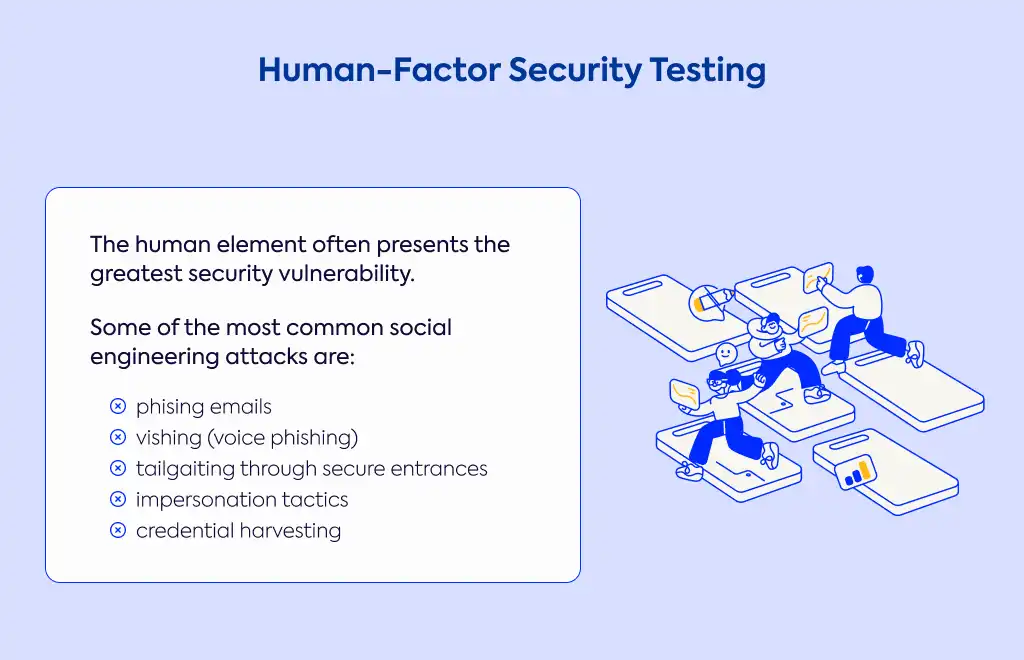
Remember that technology is only part of the equation—the human element often presents the greatest security vulnerability. Social engineering testing evaluates how susceptible your employees are to manipulation tactics like phishing emails or deceptive phone calls. These tests help measure the effectiveness of your security awareness training and determine whether staff members are following established security policies.
A comprehensive approach might include vishing attacks (voice phishing) to see if employees will divulge sensitive information during seemingly legitimate phone conversations. You might also simulate tailgating scenarios where unauthorized individuals gain physical access by simply following authorized personnel through secure entrances.
Other important tests include checking for vulnerability to impersonation tactics (such as fake delivery personnel or service technicians), evaluating responses to credential harvesting attempts where attackers Thetry to obtain passwords or usernames, and assessing how vulnerable your organization is to "crashing the joint"—a technique where attackers simply walk through front doors without being challenged.
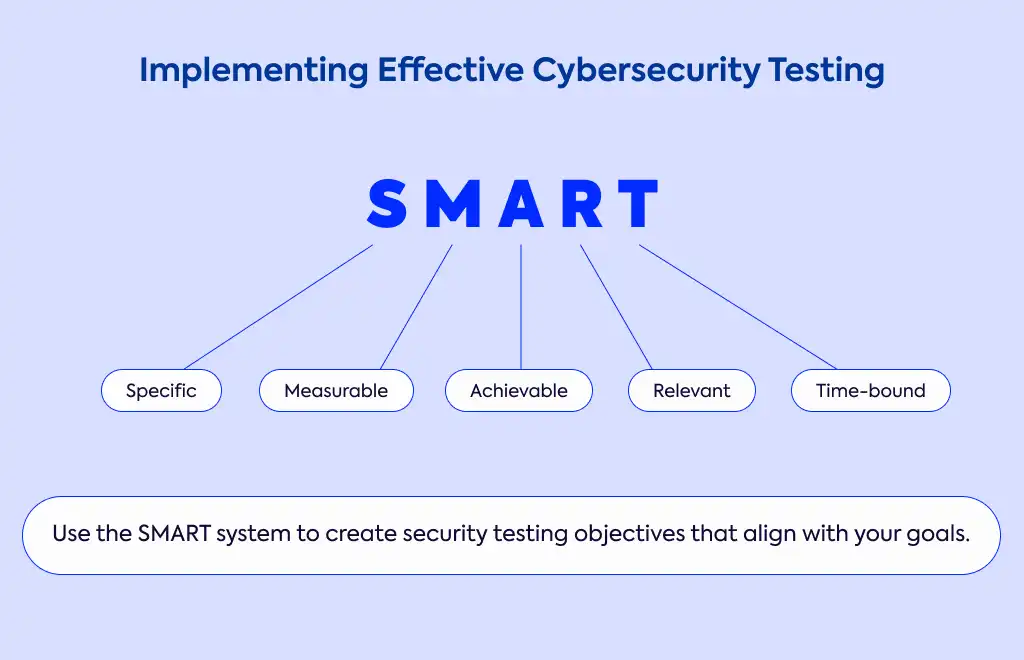
To get the most from your cybersecurity testing, start by creating a clear scope that defines precisely what is and isn't part of the testing, ensuring all parties agree on these boundaries. Then, develop specific, measurable, achievable, relevant, and time-bound (SMART) testing objectives that align with your security goals.
Select testing approaches that make sense for your specific situation, considering factors like scope, available resources, and the business risks you're trying to mitigate. Make sure you're using reputable security testing tools and services with proven track records of delivering accurate results.
Where possible, automate testing processes and run them frequently, especially after making changes to applications or infrastructure. Don't limit testing to external-facing components—internal interfaces, APIs, and user interfaces need attention too. Finally, document and report results thoroughly to stakeholders, enabling repeatable testing and ensuring everyone correctly interprets the data.
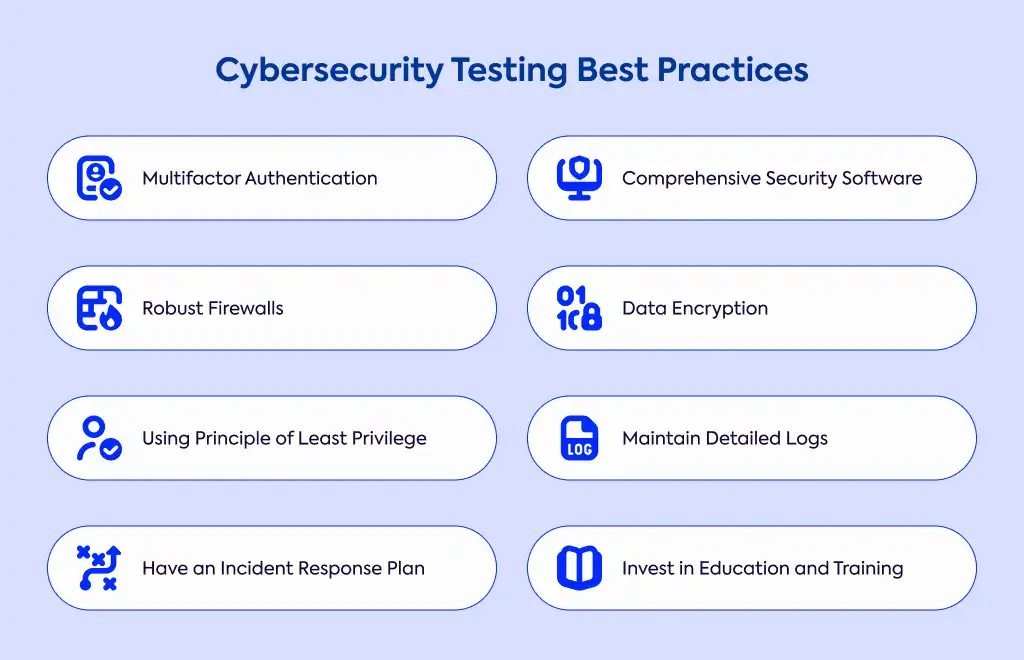
Implementing strong cybersecurity requires attention to several key practices. Start with the basics: use strong, unique passwords for all accounts and enable multifactor authentication wherever possible. Keep all your software updated with the latest security patches to address known vulnerabilities.
Make sure comprehensive security software is installed on all endpoints, including solutions for antivirus, anti-spyware, and anti-malware protection. Implement robust firewalls and secure your WiFi networks against unauthorized access.
Develop a routine for regular data backups and encrypt sensitive information to protect it even if systems are compromised. Apply the principle of least privilege by limiting user access rights to only what's necessary for their roles. Maintain detailed logs of all system activity for audit trails and potential forensic investigations.
Don't overlook mobile devices—secure them using appropriate policies and protections. Prepare for the worst by developing comprehensive incident response plans before breaches occur. Throughout all of this, strive to balance security measures with system usability to maintain operational efficiency. Finally, invest in educating and training your employees on security awareness and good email hygiene—your people are both your greatest vulnerability and your strongest defense.
Implementing comprehensive cybersecurity testing can feel overwhelming—especially when you're trying to manage multiple testing types while running your business. At Gauss, we understand these challenges and offer expert cybersecurity testing services tailored to your specific needs.
Our team of security professionals can help identify vulnerabilities in your systems before attackers do, implement the right mix of testing approaches for your organization, and develop a strategic security roadmap that protects your valuable data and reputation.
Don't wait for a breach to happen. Contact Gauss today to start a conversation about securing your digital assets with our proven cybersecurity testing expertise.