Security assessment
Protect your digital assets with proactive security assessments that uncover vulnerabilities before attackers can.
Trusted by


































What is cybersecurity?
Cybersecurity safeguards your networks, devices, and data from digital threats - preventing breaches, minimizing business disruptions, and protecting your reputation while keeping customer trust intact.
Importance of Cybersecurity
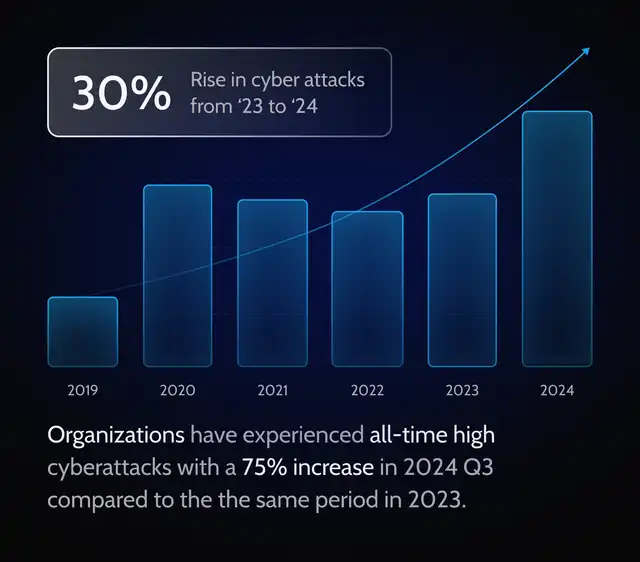

Cyber attacks are on the rise, and the risk grows every year for businesses of all sizes and industries.
As cyber attacks increase, so does the cost of cybercrime - causing trillions of dollars in damage to businesses worldwide.
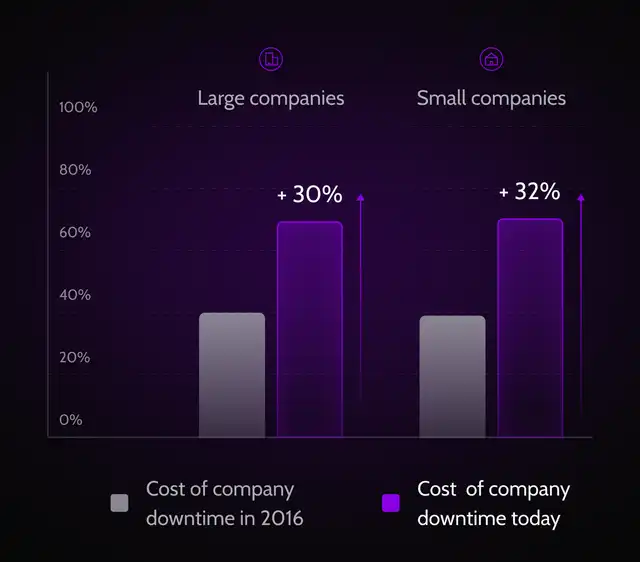
With growing reliance on digital systems, cyber attacks bring operations to a halt resulting in high downtime costs.
Technology Stack
Technology Stack

Powered by
Gauss Reflect Framework

Golang

Flutter

Angular

NodeJS

VueJS

NuxtJS

Gauss Box

Golang

Flutter

Angular

NodeJS

VueJS

NuxtJS

Gauss Box

JavaScript

TypeScript

Kubernetes

Gauss Box

Terraform

Google Cloud

Figma

JavaScript

TypeScript

Kubernetes

Gauss Box

Terraform

Google Cloud

Figma
Our security approach is tailored to your needs
Essential plan
We thoroughly examine your systems to find security gaps before attackers do. You'll receive a clear report highlighting vulnerabilities and practical steps to strengthen your defenses immediately.
Advanced plan
Beyond identifying issues, we'll guide your team with expert consultation on implementing stronger security practices. You'll gain valuable knowledge to protect your business for the long term.
Expert plan
Get complete protection with our comprehensive testing and implementation of security fixes. Optional ongoing support services are available for businesses seeking continuous monitoring and assistance.
Our process
Frequently asked questions
A cybersecurity risk assessment helps identify, analyze, and evaluate vulnerabilities and threats in your IT environment to estimate potential risk and recommend actions to protect your systems, data, and operations.
Yes. We include pen testing as part of our cybersecurity assessment, simulating real-world attacks and uncover potential weaknesses before they are exploited.
Of course! We work closely with you to deliver security measures that match your unique infrastructure, risk profile, and business processes. Our goal is to help you protect critical assets, ensure compliance, and maintain business continuity without compromise.
Absolutely! We offer blue (defensive), red (offensive), and purple (combined) team exercises to test your business defenses, identify security gaps, and strengthen your overall cybersecurity.
No, we plan and execute assessments carefully to minimize or eliminate disruptions to your business operations, ensuring your teams can continue working without interruption.
Absolutely! As part of the cybersecurity assessment, we can evaluate staff awareness and daily practices through surveys, interviews, and simulated tests to identify vulnerabilities and recommend targeted training.
We recommend conducting cybersecurity assessments at least once a year, or more frequently if there are major system changes, new compliance requirements, or emerging threats.
The duration of a cybersecurity assessment depends on the size and complexity of your environment, but most assessments typically take between 2 to 6 weeks from planning to final reporting.