Incident response
From detection to resolution, our incident response experts protect your business when every minute counts.
Trusted by


































What are Cyber attacks?
Cyber attacks are deliberate exploitations of your digital systems by malicious actors. Whether your organization has become a victim or you wish to prevent future attacks, contact us immediately to deploy our incident response team and strengthen your security posture.
Our expertise for your safety
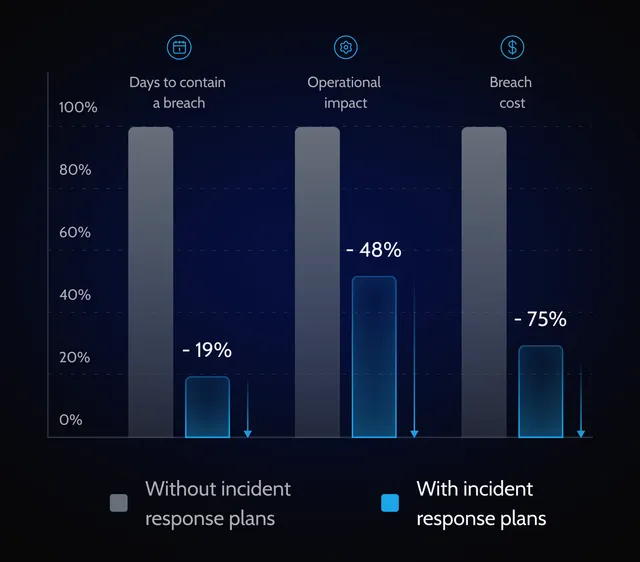
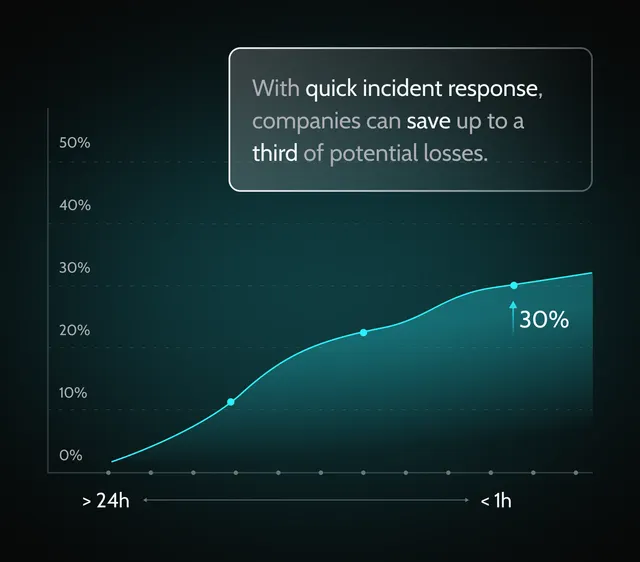
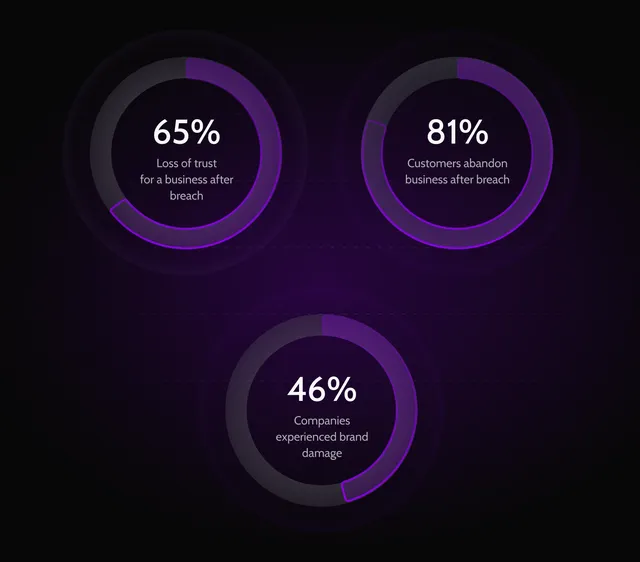
A solid cyber attack response plan helps resume operations faster, reduce losses, and cut response costs.
A fast response helps contain a cyber attack, limit damage, and prevent it from spreading across client systems.
User and customer trust is easily shaken by cyber attacks and data breaches, resulting in lost confidence and loss in profits.
Technology Stack
Technology Stack

Powered by
Gauss Reflect Framework

Golang

Flutter

Angular

NodeJS

VueJS

NuxtJS

Gauss Box

Golang

Flutter

Angular

NodeJS

VueJS

NuxtJS

Gauss Box

JavaScript

TypeScript

Kubernetes

Gauss Box

Terraform

Google Cloud

Figma

JavaScript

TypeScript

Kubernetes

Gauss Box

Terraform

Google Cloud

Figma
Most common types of cyber attacks
Malware
Computer viruses and other malicious software can steal your data, lock your files for ransom, or damage your systems -causing devastating business impacts.
Denial-of-Service attack
DoS attacks flood your network until it crashes, taking down your website and critical business systems, preventing customers and employees from accessing services.
IoT attacks
Hackers can take control of your connected devices (cameras, sensors, smart equipment, etc.), using them to steal data or access your main business network.
AI powered attacks
Attackers can trick your AI systems into making dangerous mistakes or revealing sensitive information through manipulated data inputs.
Phishing attacks
Fake emails that look legitimate trick your team into revealing passwords or installing harmful software, giving attackers easy access to your systems.
Social engineering
Attackers manipulate your employees through fake calls, messages, or direct interactions, tricking them into revealing passwords or providing system access that bypasses your security defenses.
Our process
.webp)
Got a project in mind? Let's talk business!
Schedule a meetingFrequently asked questions
Incident response is a service that is structured to detect, investigate, and resolve cybersecurity treats or breaches to minimize damage and make recovery as quick as possible.
We handle a wide range of cybersecurity threats including ransomware attacks, phishing scams, malware infections, DDoS attacks, insider threats, data breaches, and other problems your operations might experience.
Absolutely! We help you develop a new or improve an existing incident response plan that fully aligns with your business needs, regulations, and best industry practices.
Of course! We offer a full range of cybersecurity services, helping you identify the cause of the attack, analyze impacted systems, and recommend measures to prevent future incidents.
Yes, we offer incident response support with a response time of under 1 hour during working hours and within 8 hours outside of them. Our team is always on standby to help you contain threats quickly and minimize damage.
In an emergency, you can engage our services by filling out the form below or reaching out to us directly via email. We’ll respond swiftly to help you contain the threat and get your operations back on track.