25+ Custom Manufacturing Software Statistics Showcasing Efficiency Gains and Cost Reductions
Key Custom Manufacturing Software StatisticsManufacturing ...

Author:
Tomislav Horvat

· NIS2 takes effect October 18, 2024, with fines up to €10M/2% of turnover for essential entities and €7M/1.4% for important entities
· Beyond financial penalties, you face compliance orders, public disclosure requirements, and potential operational restrictions
· Executive accountability is a cornerstone of NIS2, with management facing personal liability, possible bans, and even criminal sanctions for negligence
· The hidden costs of rushed compliance and reputational damage often exceed the regulatory fines themselves
· Proactive measures like data encryption, regular security reviews, and staff training are more cost-effective than emergency remediation after enforcement begins

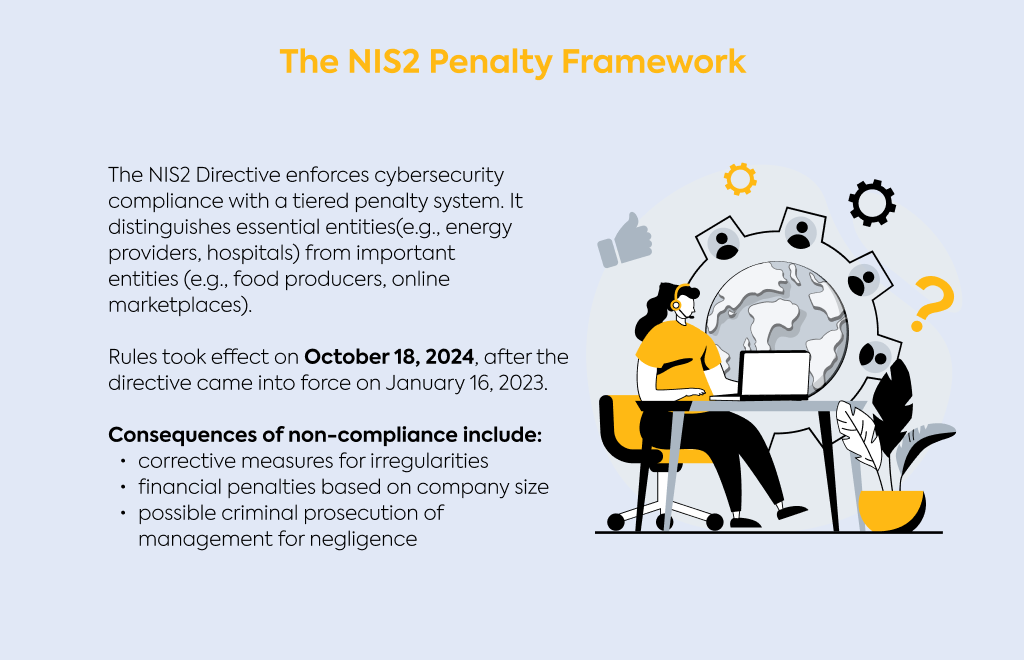
The Network and Information Security Directive 2 (NIS2) takes a firm stance on cybersecurity compliance through its tiered penalty system.
Unlike its predecessor, NIS2 clearly distinguishes between "essential entities" like energy providers and hospitals, and "important entities" such as food production companies and online marketplaces.
If you're wondering when these rules kick in, mark October 18, 2024 on your calendar.
That's when Member States must have NIS2 integrated into their national laws, having had 21 months since it came into force on January 16, 2023.
The directive doesn't just rely on fines to ensure compliance.
You'll face three potential types of consequences: non-monetary remedies like compliance orders, administrative fines scaled to your organization's size, and possibly even criminal sanctions for leadership if gross negligence is found.
What makes NIS2 different from many other regulations is its focus on accountability at the highest levels.
Your board and executive team are now directly responsible - not just your IT department.
While Member States can tailor specific implementation details, they must stick to the minimum thresholds established in the directive.
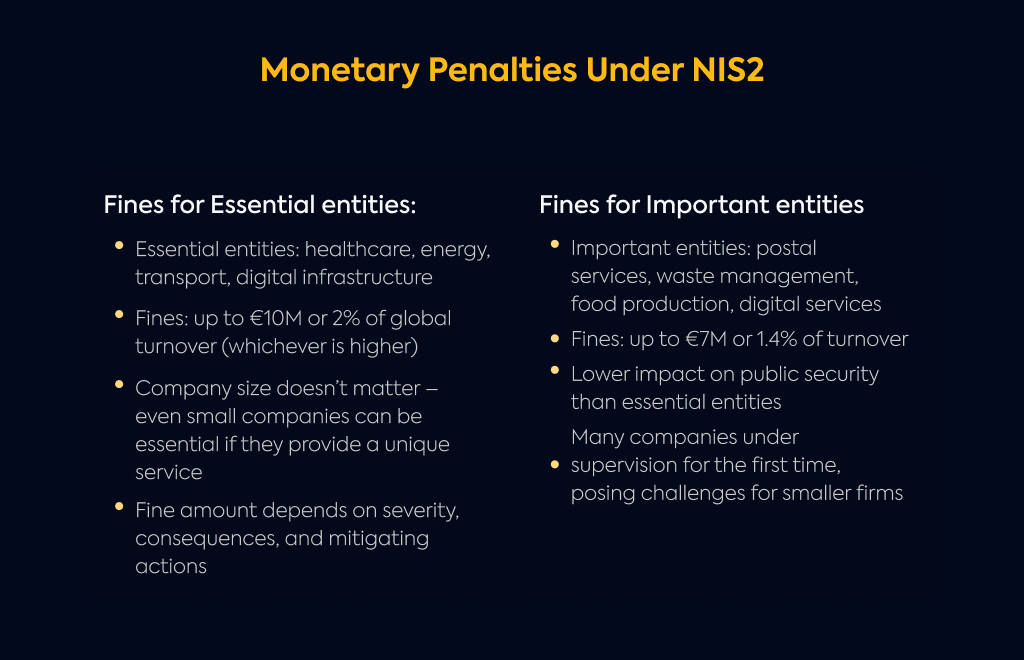
If your organization provides critical services like healthcare, energy, transport, or operates digital infrastructure, you fall into the "essential entities" category.
This classification comes with the steepest penalties - up to €10 million or 2% of your total worldwide annual turnover, whichever hits harder.
Size doesn't always matter here. Even smaller organizations can be classified as essential if they're the only provider of a critical service in a region.
The exact fine you might face depends on several factors, including how severe the violation is, what impact it had, and whether you took steps to mitigate damage.
Organizations in sectors like postal services, waste management, food production, or digital services face lower but still significant penalties.
As an important entity, you're looking at fines up to €7 million or 1.4% of worldwide annual turnover.
This lower tier recognizes that while your services matter greatly, they may not have the same immediate impact on public safety or critical infrastructure as essential entities.
Many companies now finding themselves in this category have never dealt with this kind of regulatory scrutiny before, which creates particular challenges for smaller businesses just beginning their compliance journey.
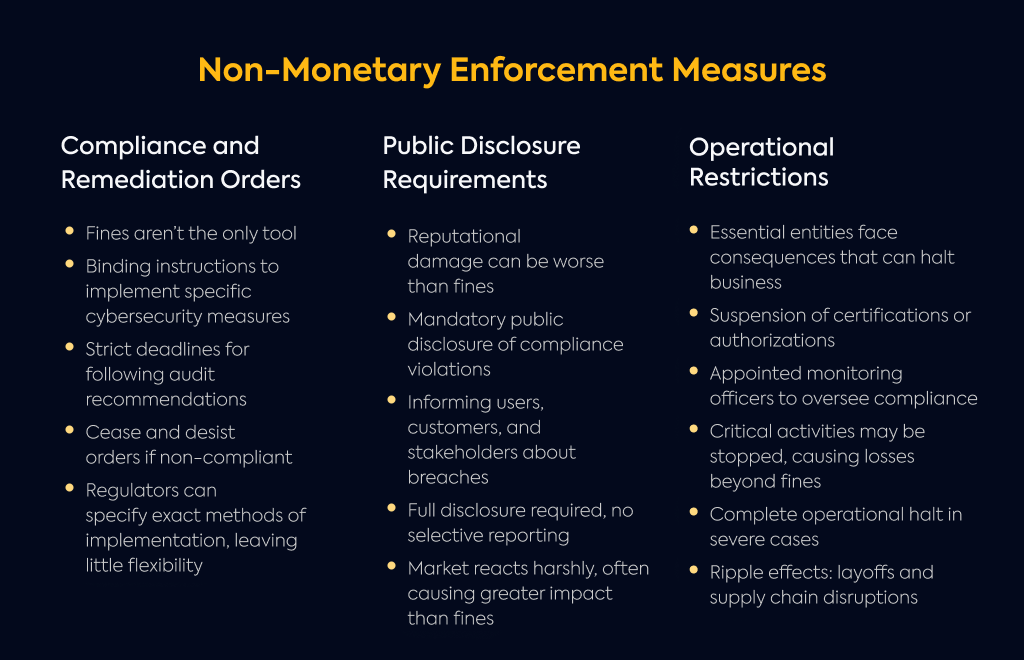
Compliance and Remediation Orders
Monetary fines aren't the only tool regulators have.
Authorities can direct your organization to implement specific cybersecurity measures through binding instructions.
ou might be ordered to follow recommendations from security audits within strict timelines.
If you're found non-compliant, expect cease and desist orders that could halt certain activities until you fix the issues.
Regulators don't just tell you what to do - they can specify exactly how to do it, requiring implementation "in a specific manner."
This leaves little room for interpretation or flexibility in how you address security gaps.
Perhaps more damaging than fines is the potential hit to your reputation.
Authorities can force you to publicly announce compliance violations.
They might issue statements naming specific individuals in your organization responsible for security failures.
You may need to inform your users, customers, and other stakeholders about cyber threats or breaches affecting them.
When incidents happen because you didn't follow NIS2 requirements, you'll have to disclose all aspects of the violation - not just the parts that make you look better.
The market tends to judge these public admissions harshly, often triggering impacts far beyond the regulatory penalty itself.
For essential entities, the consequences can directly impact your ability to do business.
Authorities might suspend certifications or authorizations your organization needs to operate.
They can appoint monitoring officers who oversee your compliance efforts for set periods.
These restrictions can stop critical business activities in their tracks, leading to financial losses beyond any fines.
In severe cases, you might need to halt operations entirely until security issues are resolved.
The ripple effects can include employee layoffs and significant business disruption that affects your entire supply chain.
NIS2 places accountability squarely at the top.
Your management team must approve cybersecurity risk management measures and oversee their implementation.
More importantly, they can be held personally liable if things go wrong.
If you serve on the board of an essential entity, you need proper training in cybersecurity best practices.
Article 20 spells this out clearly: management "can be held liable for infringements" by their organizations.
After a cyber incident, investigators will look for signs of gross negligence, which can create personal liability for executives who failed to take appropriate action.
The consequences for leadership can be severe.
If you're an executive at an essential entity with repeated violations, you might face a temporary ban from management roles.
These bans stick until the compliance issues are properly addressed.
Beyond career impact, executives can face personal fines separate from what the organization pays.
In cases of gross negligence, criminal liability enters the picture - especially if you failed to implement basic security measures.
The pain doesn't stop there, as affected parties like customers or partners might file civil lawsuits against you personally when security incidents cause them harm.

Essential entities face the strictest oversight.
Authorities can inspect your operations on-site or remotely without warning or evidence of wrongdoing.
You'll undergo regular security audits to verify ongoing compliance.
After significant security incidents, expect ad hoc audits to determine what went wrong and identify security gaps.
Regulators will evaluate your security through various means, including scanning your systems, requesting documentation, and verifying proper implementation of required measures.
This proactive approach means you need to maintain compliance at all times, not just when you think someone's watching.
If you run an important entity, you'll face a somewhat lighter touch.
Authorities typically only inspect your operations when they suspect possible violations.
You might undergo targeted security audits by independent bodies or by the authorities themselves.
Regulators will verify your compliance through security scans and document reviews.
This more reactive approach reflects the different risk profile of important entities.
However, when concerns arise, trained professionals will still conduct thorough inspections, so maintaining proper security practices remains essential.

The financial impact of non-compliance extends far beyond official fines.
When regulators force you to implement security measures quickly, you'll make rushed decisions that often cost more than planned approaches would have.
You might need to hire external consultants for emergency help or conduct additional security audits under pressure.
Expect to make urgent investments in new staff, process restructuring, and comprehensive employee training.
You'll need to acquire advanced security tools and frameworks faster than your budget planning allowed for.
These hasty implementations typically cost significantly more than if you'd taken a methodical approach to compliance from the start.
The difference can sometimes exceed the potential fines themselves, making proactive compliance the more cost-effective choice.
Money isn't everything.
Security incidents and compliance violations erode trust that took years to build.
Your customers might reconsider their relationship with you, and stakeholders could lose confidence in your leadership.
After NIS2 violations become public, negative media coverage can damage your brand and reduce your market value.
Partners and clients increasingly view compliance warnings as red flags about your security practices.
As businesses try to minimize their own risk exposure, many now prefer to work only with NIS2-compliant partners, creating a competitive disadvantage for non-compliant organizations.
Even staffing becomes harder when your security reputation suffers.
Top IT security professionals tend to avoid companies with questionable security practices, making it harder to build the team you need to fix the problems.

Starting your compliance journey doesn't have to be overwhelming.
Begin by conducting a thorough audit to identify all your data storage locations, including cloud services and SaaS applications that might not be on your radar.
Make it a habit to regularly review your cybersecurity tools and strategies before problems arise.
Implement encryption for data both in transit and at rest as a fundamental security measure.
Don't forget to establish reliable backup solutions for all your data, including information stored in SaaS applications that you might assume is already protected.
Develop comprehensive disaster recovery and business continuity strategies, and test them regularly to ensure they work when needed.
Provide all staff with initial and refresher cybersecurity awareness training, as human error remains a major vulnerability.
Finally, implement strong access controls using approaches like zero trust architecture, role-based access, permission management, and multi-factor authentication.
These practical steps will help you avoid the significant penalties and business disruption that come with non-compliance.

Feeling overwhelmed by NIS2 compliance requirements and the steep penalties for getting it wrong? You're not alone.
The technical demands, executive accountability, and looming deadlines create real pressure for organizations of all sizes.
At Gauss, we understand these challenges and provide a comprehensive list of cybersecurity services to address your specific compliance needs.
Our team can help you implement the right security measures, establish proper monitoring systems, and create the documentation framework you need - all while avoiding the costly rush of last-minute compliance.
Why struggle through complex technical requirements when you can have a partner who specializes in turning regulatory challenges into smoothly functioning systems?
Contact us today to start a conversation about securing your organization against NIS2 penalties.