25+ Custom Manufacturing Software Statistics Showcasing Efficiency Gains and Cost Reductions
Key Custom Manufacturing Software StatisticsManufacturing ...

Author:
Tomislav Horvat

The Network and Information Systems Security Directive 2 (NIS2) is the European Union's updated legislative framework for cybersecurity, enacted to strengthen the security of network and information systems across the EU. NIS2 entered into force on January 16, 2023, replacing the original NIS Directive from 2016, which had proven insufficient for addressing the rapidly evolving cybersecurity threat landscape.
Member States have until October 17, 2024, to transpose NIS2 into national law. Once implemented, covered entities will need to comply with its provisions immediately. The directive significantly expands the scope of sectors considered critical to the EU economy and society, covering energy, transport, banking, healthcare, digital infrastructure, public administration, and many others.
NIS2 distinguishes between "essential" and "important" entities based on the criticality of their services, applying stricter supervision to essential entities while maintaining proportionate requirements for important ones. All medium-sized and large companies (those with more than 50 employees and annual turnover exceeding €10 million) operating within the covered sectors must comply with the directive's requirements.
With potential penalties of up to €10 million or 2% of global annual turnover for non-compliance, organizations should begin their compliance journey now rather than waiting for the transposition deadline. This checklist provides a practical, step-by-step approach to achieving and maintaining compliance with NIS2.
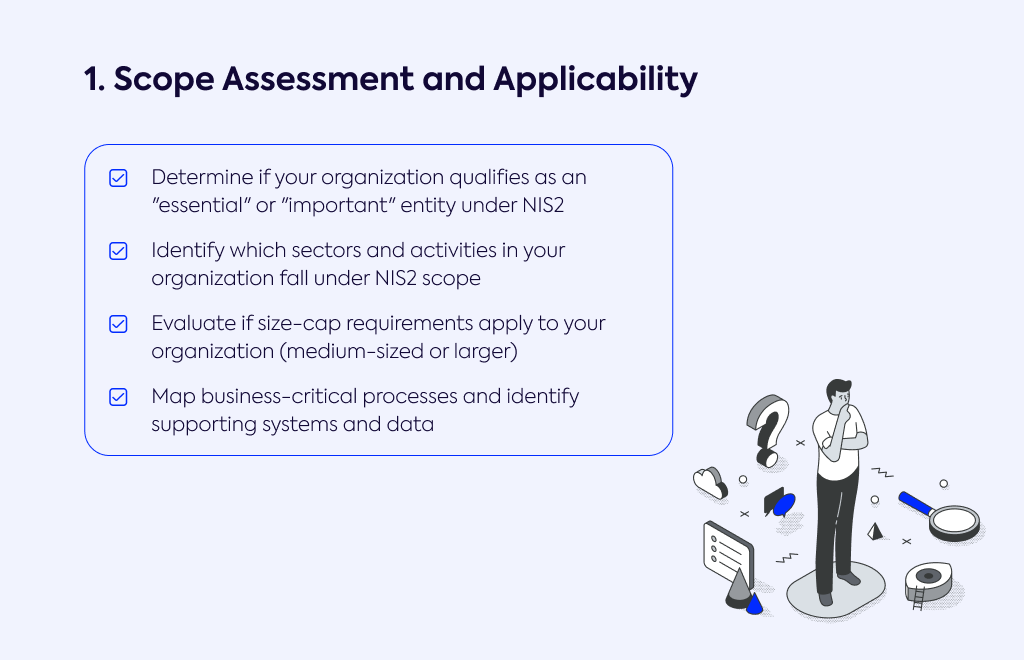
Determine if your organization qualifies as an "essential" or "important" entity under NIS2
Identify which sectors and activities in your organization fall under NIS2 scope
Evaluate if size-cap requirements apply to your organization (medium-sized or larger)
Map business-critical processes and identify supporting systems and data
Why this matters: Determining your organization's classification is the foundation of NIS2 compliance. Article 2 and Annexes I and II define which entities fall under the scope - from energy and healthcare to digital infrastructure and manufacturing. The size-cap rule (medium-sized or larger, per Article 6) applies with exceptions for certain critical smaller entities. Without this step, you cannot identify your specific obligations or the appropriate level of measures required to ensure compliance with the directive's proportionality principle.
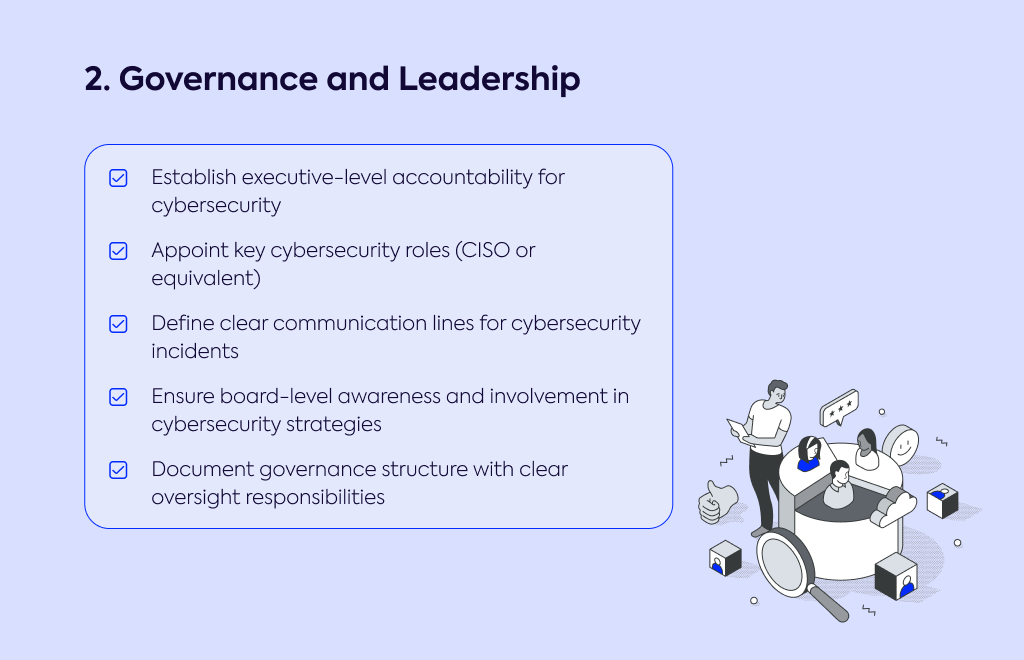
Establish executive-level accountability for cybersecurity
Appoint key cybersecurity roles (CISO or equivalent)
Define clear communication lines for cybersecurity incidents
Ensure board-level awareness and involvement in cybersecurity strategies
Document governance structure with clear oversight responsibilities
Why this matters: Article 20 mandates management accountability, requiring oversight and approval of cybersecurity measures, with potential personal liability for non-compliance. While appointing a CISO isn't explicitly required, Article 21 implies the need for defined roles and responsibilities. Strong governance ensures decisions about security investments are made at the appropriate level and demonstrates to regulators that cybersecurity is taken seriously by leadership.
Conduct comprehensive cybersecurity risk assessment
Document organizational goals and acceptable risk levels
Implement risk management framework aligned with NIS2 requirements
Evaluate internal and external risk factors
Implement controls to address identified risks or document accepted risks
Why this matters: A risk management framework is a core requirement under Article 21(1), which requires entities to adopt risk management measures with policies on risk analysis and security measures. Documenting your acceptable risk levels provides justification for your security decisions during audits. This risk-based approach allows you to prioritize resources based on the most significant threats to your critical systems.
Develop and implement cybersecurity policies
Implement technical security controls aligned with NIS2 requirements
Establish secure system design procedures and continuous monitoring
Implement encryption and cryptography policies
Deploy multi-factor authentication for critical systems
Implement vulnerability management procedures
Establish security measures for cloud environments and SaaS applications
Why this matters: Article 21(2) lists minimum security measures, including policies on information system security, cryptography, access control, and vulnerability management. These technical controls form the backbone of your security posture. While specific technologies like MFA aren't explicitly mandated, they represent standard practices for implementing the required "access control measures" - especially for critical systems. Cloud/SaaS security measures ensure you maintain security across all operational environments.
Identify critical third-party suppliers and service providers
Assess security posture of vendors and service providers
Implement safeguards for data exchange with third parties
Include security requirements in contracts with third parties
Monitor supply chain risks continuously
Evaluate security of third-party integrations and APIs
Why this matters: Article 21(2)(d) requires entities to address supply chain security, including assessing supplier cybersecurity practices and incorporating security into contracts. This reflects the reality that many modern cyberattacks target third-party vulnerabilities to compromise primary targets. Securing your supply chain means ensuring that your vendors meet security standards commensurate with the criticality of the services they provide to your organization.
Develop formal incident response plan
Establish backup management processes
Create disaster recovery plans with clear priorities
Define recovery time objectives (RTOs)
Implement crisis management procedures
Document business continuity policies
Schedule regular testing of backup and recovery processes
Why this matters: Article 21(2)(f) requires measures for business continuity, including backup management and disaster recovery. Incident response plans are mandated under Article 21(2)(e). The ability to recover quickly from cybersecurity incidents is crucial to maintaining essential services. Regular testing ensures these plans work when needed - theoretical plans that don't function during a real incident won't satisfy regulators or protect your operations.

Establish procedures for detecting and reporting cyber incidents
Implement mechanisms to meet 24-hour initial notification requirements
Create processes for complete incident reporting within required timeframes
Document incident response workflows and responsibilities
Implement ticketing system for tracking incidents
Why this matters: Article 23 mandates incident reporting with strict timelines: 24-hour early warning, 72-hour detailed notification, and a final report within one month. These reporting obligations are non-negotiable under NIS2 and require robust detection capabilities and clear escalation procedures. While a ticketing system isn't explicitly required, it represents a practical approach to managing incidents and maintaining the documentation trail needed to demonstrate compliance.

Provide regular cybersecurity training for all employees
Conduct phishing and social engineering awareness campaigns
Ensure stakeholders understand their responsibilities under NIS2
Document training procedures and participation
Why this matters: Article 21(2)(h) requires measures to ensure employee awareness of cyber threats, including training. The human element remains one of the most significant vulnerabilities in any cybersecurity program. Training must be ongoing, as threats evolve constantly, and documentation of this training provides evidence of compliance during audits. Phishing simulations provide practical experience in identifying common attack vectors.
Implement continuous monitoring of security controls
Conduct regular security audits and reviews
Perform penetration testing and vulnerability assessments
Verify data integrity of backup systems
Document all audit activities and findings
Why this matters: Article 21(2)(b) requires policies to evaluate security measure effectiveness, implying continuous monitoring and audits. Vulnerability assessments and penetration testing are standard practices for identifying weaknesses before attackers do. Regular verification of backup integrity ensures that recovery options will function when needed. Documentation of all these activities provides evidence of due diligence during regulatory reviews.
Map NIS2 requirements to your organization's operations
Document all cybersecurity measures and compliance efforts
Establish procedures to verify compliance regularly
Prepare for potential regulatory audits
Review and update documentation as systems and processes change
Why this matters: Article 24 requires entities to provide evidence of compliance, including documentation of measures and processes. Comprehensive documentation is crucial during audits and investigations, particularly for essential entities subject to proactive supervision. This documentation needs to evolve with your systems and processes, demonstrating ongoing compliance rather than a one-time effort.

Monitor the cybersecurity landscape for new threats
Update security measures based on evolving threats
Participate in industry forums to stay updated on best practices
Regular review and update of risk assessments
Test and refine incident response capabilities regularly
Why this matters: Article 21 implies continuous improvement by requiring "appropriate and proportionate" measures that evolve with risks. Cybersecurity is not a static field - new threats emerge constantly, and defensive measures must adapt accordingly. While participation in industry forums isn't explicitly mandated, Article 14 encourages information sharing, and these forums provide valuable intelligence on emerging threats and defensive strategies.
Navigating NIS2 compliance requirements can be overwhelming, especially with Croatia's additional cybersecurity requirements going beyond the EU baseline. The stakes are high – non-compliance could result in penalties of up to €10 million or 2% of annual turnover, and management can be held personally liable.
Gauss can help you navigate this complex regulatory landscape.
As an experienced IT company specializing in custom solutions, Gauss has the expertise to build and implement the technical security controls required by NIS2. Our team understands both the EU-wide requirements and Croatia's specific implementation, which sets very detailed security measures beyond NIS2 requirements including specific password policies and enhanced security protocols.
Don't risk non-compliance. Our cybersecurity experts can:
Assess your current security posture against NIS2 requirements
Develop custom solutions that address compliance gaps
Implement the technical controls needed for both core NIS2 and Croatia-specific regulations
Provide ongoing monitoring and support to maintain compliance as threats evolve
Contact Gauss Today to discuss how we can help you achieve and maintain NIS2 compliance while strengthening your overall cybersecurity posture.