25+ Custom Manufacturing Software Statistics Showcasing Efficiency Gains and Cost Reductions
Key Custom Manufacturing Software StatisticsManufacturing ...

Author:
Tomislav Horvat

Expanded Scope and Timeline: NIS2, the EU's most comprehensive cybersecurity legislation to date, came into effect January 2023, with Member States required to implement it by October 17, 2024. It categorizes organizations as "Essential" or "Important" Entities with different oversight levels.
Applicability and Compliance: Medium (50+ employees/€10M+ turnover) and large organizations (250+ employees/€50M+ turnover) typically fall under scope. Non-EU companies must consider NIS2 when doing business with EU entities due to supply chain requirements.
Core Requirements: Organizations must implement ten mandatory cybersecurity measures covering risk analysis, incident handling, business continuity, supply chain security, and multi-factor authentication. Management is now directly accountable for cybersecurity failures.
Strict Reporting Obligations: Significant incidents require notification within 24 hours, follow-up assessment within 72 hours, and comprehensive reporting within one month.
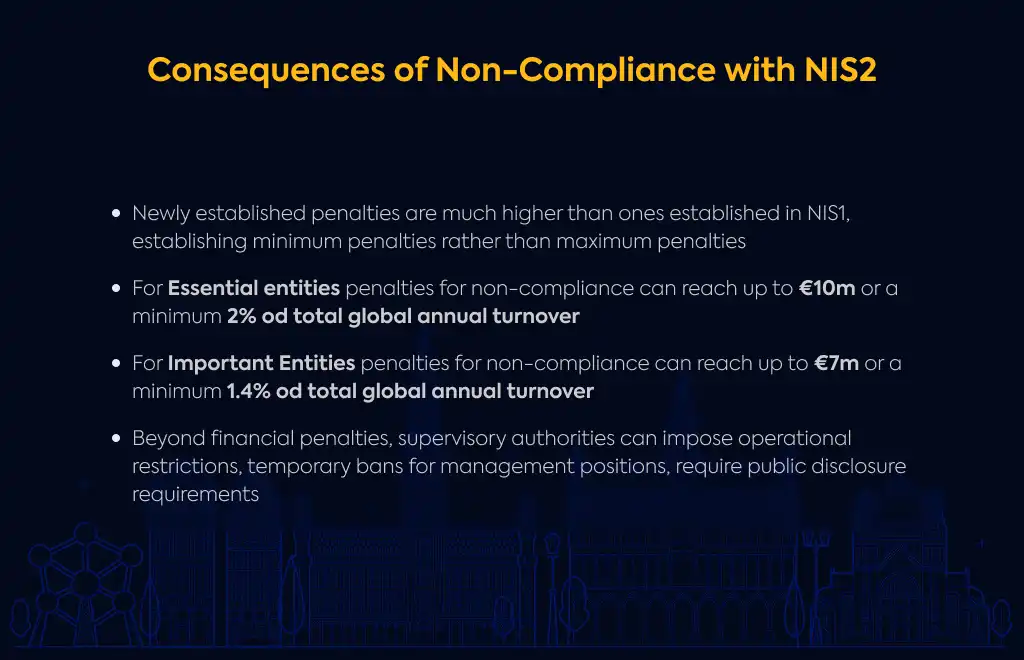
Severe Penalties: Non-compliance can result in fines up to €10 million/2% of global turnover for Essential Entities (€7 million/1.4% for Important Entities), operational restrictions, management bans, and reputational damage.
Implementation Strategy: Success requires gap analysis, executive buy-in, a comprehensive risk management framework, robust incident response processes, and leveraging existing standards like ISO 27001 to avoid duplicating efforts.
Let's talk about the NIS2 Directive, which the EU adopted in December 2022. It came into effect in January 2023, and Member States need to incorporate it into their national laws by October 17, 2024. This directive isn't just another regulation – it's actually the EU's most comprehensive cybersecurity legislation to date.
So what's it trying to accomplish? At its core, NIS2 aims to strengthen security requirements, tackle supply chain vulnerabilities, make reporting processes more streamlined, introduce stronger supervision, and create consistent sanctions across the EU.
The new directive significantly expands on the original 2016 version. One major change is how it categorizes organizations. Instead of the previous Operators of Essential Services and Digital Service Providers, we now have "Essential Entities" and "Important Entities," each with different levels of oversight. This shift reflects the growing cyber threats that come with our increasingly digital world.
NIS2 sets up minimum rules for a regulatory framework and helps Member States collaborate more effectively. Think of it as creating a more level playing field across the EU market by aligning security requirements, how incidents are reported, and enforcement measures.
What's particularly noteworthy is that for the first time, NIS2 addresses ICT supply chain security and introduces management accountability – meaning executives are now directly responsible when cybersecurity measures fail. This represents a significant shift in how responsibility is allocated.

You might be wondering if NIS2 applies to your organization. The directive divides covered entities into two categories: Essential Entities and Important Entities.
Essential Entities include organizations in sectors like energy, transport, banking, healthcare, water, digital infrastructure, ICT service management, public administration, and space. Important Entities, on the other hand, cover areas such as postal services, waste management, chemicals, food production, manufacturing, digital providers, and research organizations.
Size typically matters when determining if you're covered. Generally, medium organizations (with 50+ employees or €10M+ turnover) and large organizations (with 250+ employees or €50M+ turnover) fall under the scope. That said, there are some exceptions that bring entities into scope regardless of size – for example, if you're a sole service provider in your area, if your operations could potentially impact public safety, or if you've been designated as critical.
Some sectors get exemptions, including defense, national security, public security, law enforcement, and judiciary entities.
Here's something important to note – even if your company isn't based in the EU, you still need to consider NIS2 when doing business with EU entities because of the supply chain requirements. EU organizations will be looking closely at their non-EU suppliers and might require contractual security commitments from you. And this isn't just a European trend – similar cybersecurity laws are emerging around the world, creating parallel compliance requirements you'll need to navigate.

NIS2 requires organizations to implement ten specific cybersecurity risk management measures. Let's walk through them.
First, you'll need policies for risk analysis and information system security, which includes guidance for your staff on IT security practices. You'll also need incident handling procedures that cover how to prevent, detect, and respond to security incidents.
Business continuity is another key area – you'll need measures for backup management and disaster recovery to keep operations running when things go wrong. Supply chain security is equally important, requiring protocols that address your relationships with suppliers and service providers.
You'll need security measures covering how you acquire, develop, and maintain your network and information systems. To make sure everything's working properly, you'll need policies and procedures to test and audit the effectiveness of your risk management measures.
Other requirements include implementing basic cyber hygiene practices and cybersecurity training for all your staff, having policies for using cryptography and encryption where appropriate, and putting in place human resources security, access control policies, and asset management protocols.
Finally, you'll need to implement multi-factor authentication (or continuous authentication solutions) and secure communications to protect access to your systems.

One of the biggest shifts in NIS2 is the focus on leadership responsibility. Your management team must now approve the cybersecurity risk management measures implemented by your organization. Executives need to actively supervise the implementation of security measures – and they're accountable if compliance fails.
This means your top managers need regular cybersecurity training to gain enough knowledge to properly assess risks. It's not just organizational liability anymore – management bodies bear personal liability for cybersecurity failures.
Senior leadership can't just delegate cybersecurity to technical teams – they need to take active roles in cybersecurity governance. Board-level involvement becomes mandatory rather than optional, with regular cybersecurity updates and reviews presented to management bodies.
In essence, cybersecurity is now firmly a leadership responsibility, not just a technical concern. Your management team needs to establish clear governance structures with assigned responsibilities to maintain ongoing compliance.

NIS2 introduces strict timelines for incident reporting. If a significant incident occurs, you'll need to provide initial notification to the relevant authorities within 24 hours of becoming aware of it. You'll need to indicate whether you suspect the incident was caused by unlawful or malicious acts.
Within 72 hours, you'll need to provide a follow-up notification that includes an initial assessment of severity and impact. If available, you should also include indicators of compromise in this 72-hour notification.
A month after your initial report, you'll need to submit a final comprehensive report that includes a detailed incident description, the threat type or root cause, and what mitigation measures you applied.
For incidents that are still ongoing, you'll need a progress report at the one-month mark and a final report after resolution. You might also need to provide intermediate status updates if requested by competent authorities or the Computer Security Incident Response Team (CSIRT).
Don't forget that you'll also need to notify the recipients of your services if the incident is likely to adversely affect your service provision to them.

Supply chain security is a major focus in NIS2. You'll need to assess the overall quality and resilience of products and services throughout your supply chain, including evaluating the cybersecurity risk-management measures built into your suppliers' products and services.
Take time to review your suppliers' secure development procedures and cybersecurity practices. You'll need to incorporate cybersecurity risk-management measures into your contractual arrangements with direct suppliers.
Look beyond just your direct suppliers – consider risks that might come from other levels of suppliers and service providers further down the chain. Pay particular attention to evaluating Managed Security Service Providers that handle critical functions like incident response or penetration testing.
Regular audits and reviews will help ensure your suppliers' cybersecurity practices align with your security policies. Consider implementing a vendor risk management program to systematically assess third-party security policies and practices.
Finally, coordinate risk assessments of critical ICT services, systems, or products, looking at relevant threats and vulnerabilities that could affect your operations.
The stakes for non-compliance with NIS2 are quite high. For Essential Entities, financial penalties can reach up to €10 million or at least 2% of total global annual turnover (whichever is higher) for violations of risk management and reporting obligations. Important Entities face penalties up to €7 million or at least 1.4% of total global annual turnover.
It's worth noting that the directive establishes minimum rather than maximum penalties, so actual fines could potentially be higher depending on implementation by Member States.
Beyond financial penalties, supervisory authorities can impose operational restrictions. These might include temporarily suspending certifications or authorizations, conducting mandatory audits, or even appointing monitoring officers to oversee your operations.
The personal liability aspect is particularly notable – management bodies face potential temporary bans from management positions. For instance, individuals in CEO or legal representative roles found responsible for non-compliance could be barred from their positions.
There are also public disclosure requirements where authorities can compel your organization to publish information about non-compliance aspects. This kind of public exposure can cause significant reputational damage that might last long after you've addressed the compliance issues.
Non-compliance can also lead to losing business opportunities as partners terminate relationships with non-compliant entities to mitigate their own supply chain risks under NIS2.
The long-term business consequences of inadequate cybersecurity measures extend beyond regulatory penalties. System downtime, for example, costs approximately €9,000 per minute for large enterprises, while data breaches average around €4.35 million globally.
Remember that Member States can supplement the EU-mandated penalties with additional national sanctions and enforcement measures. Regulators may even issue public statements identifying specific people responsible for violations, creating personal and professional consequences beyond formal penalties.
The first step in your compliance journey should be a thorough gap analysis. Start by creating a detailed inventory of all your digital assets, systems, and services that fall under NIS2's scope. Document your existing security policies, procedures, and technical controls across the organization.
Compare your current security approach against the 10 mandatory risk management measures we discussed earlier. Where do you see gaps in your risk management, incident response, or reporting capabilities?
Take a close look at your supply chain security and vendor management processes. How do they stack up against NIS2 requirements? Similarly, evaluate how mature your access controls and authentication mechanisms are.
Review your business continuity and disaster recovery plans to see if they're effective enough. Check if your existing documentation aligns with NIS2 reporting requirements.
Once you've identified all the gaps, prioritize them based on risk level and compliance impact. This will help you focus your remediation efforts where they matter most.
Getting your leadership team on board is crucial for successful NIS2 compliance. Start by educating your top management about the sanctions and personal liability provisions in NIS2. Help them understand the financial implications of non-compliance, including potential fines and penalties.
Don't just focus on the negative – highlight the competitive advantages that come with a strong cybersecurity posture. Show how NIS2 compliance aligns with your broader business objectives and risk management strategies.
Develop a clear budget proposal that outlines necessary investments and the expected return. Consider presenting a phased implementation approach with clear milestones and deliverables to make the process more manageable.
NIS2 requires executive-level cybersecurity awareness training, so organize these sessions for your leadership team. Create a governance structure that clearly defines executive roles and responsibilities for cybersecurity.
To keep everyone informed, establish regular reporting mechanisms that update leadership on your compliance progress.
With your leadership on board, it's time to develop a robust risk management framework. Take a risk-based approach that prioritizes your most critical systems and sensitive data. Define clear roles and responsibilities for cybersecurity across your organization.
Create a comprehensive set of security policies that align with the 10 NIS2 risk management measures. Develop procedures for conducting regular risk assessments and managing vulnerabilities effectively.
To measure your progress, establish metrics and key performance indicators for security effectiveness. Where possible, align your risk management framework with existing standards like ISO 27001 to avoid duplicating efforts.
Implement security controls that are proportionate to the identified risks for each system or service. Document your security architecture, making sure it addresses protection, detection, and response capabilities.
Finally, establish governance processes for regularly reviewing and updating your risk framework as your organization and the threat landscape evolve.
Given NIS2's strict reporting requirements, you'll need a robust incident response capability. Create a formal incident response plan that clearly defines roles, responsibilities, and procedures. Implement detection and monitoring systems that can identify potential security incidents early.
Define incident classification criteria and reporting thresholds that align with NIS2 requirements. Establish communication channels with relevant authorities and CSIRTs so you know exactly who to contact when an incident occurs.
Create templates for the required 24-hour, 72-hour, and one-month incident reports to speed up your response during an actual incident. Develop procedures for collecting and preserving evidence during incident investigations.
Test your incident response procedures through regular drills and simulations. After each exercise (and after real incidents), conduct post-incident reviews to incorporate lessons learned and continuously improve your response capabilities.
Make sure you have the technical capabilities to identify indicators of compromise for reporting purposes, as these details are required in your notifications.

Let's talk about putting effective risk management into practice. Rather than jumping straight to solutions, you'll want to start with a thoughtful approach to identifying, assessing, and prioritizing your cybersecurity risks.
Think of your security policies as your organization's security constitution - they need to be comprehensive enough to cover all the bases, but clear enough that people can actually follow them. The key is making them practical, not just theoretical documents that gather dust on a digital shelf.
When it comes to risk assessments, regularity matters more than perfection. Set up a cadence for checking your critical systems and applications that makes sense for your business rhythm. For vulnerability management, you'll need more than just scanning tools - you need a process that helps you decide which vulnerabilities to tackle first based on your specific business context.
Asset management might sound boring, but you can't protect what you don't know you have. A good inventory of systems and data is like a map - it shows you what you're working with and where your sensitive information lives. Speaking of which, data classification doesn't have to be complicated - even simple tags like "public," "internal," or "restricted" can make a huge difference in how people handle information.
Don't forget about your vendors - they often have keys to your digital kingdom. Develop ways to assess their security practices before you hand over access. And whenever you're building or buying new systems, make security architecture reviews part of the conversation from day one, not an afterthought.
We all know Murphy's Law - anything that can go wrong, will go wrong. That's why solid business continuity plans aren't a luxury - they're a necessity. Focus on keeping your most critical business functions running when disruptions hit.
Think of backup procedures like insurance - you hope you never need them, but you're really glad they're there when you do. And don't just back up your data - test restoring it regularly to make sure your safety net actually works.
When crisis hits, everyone needs to know their role. Create crisis management teams where everyone understands exactly what they're responsible for. Clear communication chains are vital too - both for keeping your team in the loop and for updating external stakeholders appropriately.
Business impact analyses help you understand what matters most - which processes and systems would cause the biggest problems if they went down? Once you know that, you can prioritize your recovery efforts accordingly.
Practice makes perfect, so run tabletop exercises and simulations regularly. They don't have to be elaborate productions - even simple scenarios can reveal gaps in your response plans. And have a plan B for your physical locations - if your main office becomes unusable, where will critical staff work instead?
Passwords alone just don't cut it anymore. Adding multi-factor authentication is like adding a deadbolt to your door - it significantly raises the bar for attackers. For systems containing your crown jewels, consider solutions that continuously verify identity throughout a session, not just at login.
The principle of least privilege is simple but powerful: give people only the access they need to do their jobs, nothing more. It's like having different keys for different rooms in your building - not everyone needs access everywhere. And just like you might change locks when tenants move out, regularly review user access rights to prevent "access creep" over time.
Remote work has changed the game for access security. Make sure your remote access solutions include appropriate authentication safeguards. Pay special attention to privileged accounts - they're like master keys, so they need extra protection and oversight.
For particularly sensitive functions, consider implementing separation of duties - requiring more than one person to complete critical processes. It's the digital equivalent of requiring two keys to launch a missile. And keep an eye out for unusual login patterns - if someone typically logs in from Berlin during business hours, a 3 AM login from overseas should raise red flags.
Think of encryption as the diplomatic pouch of the digital world - ensuring messages and data can't be tampered with or read by the wrong people. You need strong encryption both for data at rest and for information traveling across networks.
Transport layer security (TLS) has become table stakes for network communications - it's the baseline, not an extra. But encryption is only as good as your key management. Keys need to be generated securely, distributed carefully, and rotated regularly - just like you'd change the locks if too many copies of a physical key were floating around.
Your cryptographic keys deserve bank-vault level protection. After all, if someone gets your keys, your encryption might as well not exist. When choosing encryption methods, match the strength to the sensitivity - you might use different locks for your garden shed versus your safe deposit box.
Before bringing third-party products into your environment, take time to evaluate their cryptographic implementations. Not all encryption is created equal, and vulnerabilities in how it's implemented can undermine otherwise strong security. Don't forget about mobile devices and removable media - they often contain sensitive information but can be easily lost or stolen.
And when data reaches the end of its useful life, you need secure processes for permanently removing it. Simply hitting delete usually isn't enough - it's more like throwing away a letter without shredding it first.
Your technology can be fort knox, but if someone props open the door, those defenses don't matter much. That's why comprehensive security awareness training is so important for everyone in your organization. People aren't born knowing good security practices - they need to learn them.
Staff who handle sensitive systems or data need specialized training beyond the basics. Think of it like defensive driving courses for people operating heavy machinery - the stakes are higher, so the training needs to be more intensive.
IT administrators and developers need role-specific training focused on the unique security challenges they face. Regular phishing simulations help everyone stay sharp - they're like fire drills for your email inbox.
Use multiple channels for your security awareness campaigns - posters, newsletters, team meetings, intranet articles. People learn differently, so variety helps reinforce the message. New employee onboarding is a golden opportunity to establish good security habits from day one, before bad habits can form.
Measure the effectiveness of your training programs - are people actually changing their behavior, or just clicking through slides? And don't forget about contractors and third parties who access your systems - they need to follow your security rules too.
Finally, make sure your executives get proper cybersecurity training. NIS2 requires it, but more importantly, security culture flows from the top. When leaders understand and prioritize security, everyone else tends to follow suit.

Think of your incident response plan as your cybersecurity emergency playbook - when trouble hits, you won't have time to figure things out from scratch. Those tight NIS2 reporting deadlines mean you need to have your game plan ready to go.
Your plan should map out the journey from first spotting a problem all the way through to resolving it. It's like creating an emergency contact list for your home - everyone needs to know exactly who does what when things go sideways. Who makes the calls? Who investigates? Who decides when to escalate? Spell it all out clearly.
Different types of security incidents require different responses. A ransomware attack needs different handling than a data breach or a denial-of-service attack. Your plan should be like a choose-your-own-adventure book with clear paths for various scenarios you might face.
Decision-making can get murky during a crisis, so establish clear escalation paths ahead of time. It's a bit like hospital triage - you need to know who has the authority to make critical decisions when minutes count. And just like at a crime scene, you'll need procedures for preserving digital evidence without contaminating it.
Save yourself precious time by creating fill-in-the-blank templates for documenting incidents. After the dust settles, build in time for a "lessons learned" review - what worked, what didn't, and what you'll do differently next time.
Remember that incidents often trigger both your response plan and your business continuity plan. Make sure these two plans talk to each other - think of them as two emergency services that need to coordinate at the scene of an accident.
NIS2 doesn't require you to report every little hiccup - only "significant incidents." But what counts as significant? That's where you need to roll up your sleeves and define what "severe operational disruption" means for your specific business. Is it when your customer-facing systems go down? When certain data is compromised? When operations in multiple locations are affected?
You'll also need to set thresholds for "considerable material or non-material damage." Material damage might include financial losses, while non-material could involve reputation or customer trust. It's like setting the smoke detector sensitivity in your house - too sensitive and you're always responding to burnt toast, not sensitive enough and you might miss a real fire.
The clock starts ticking as soon as you become aware of a significant incident. Within 24 hours, you need to make your initial notification. Think of this as the cybersecurity equivalent of calling 112 (European emergency number) - you're letting authorities know something's happening, even if you don't have all the details yet.
By the 72-hour mark, you need a more substantial follow-up that includes your initial assessment of how bad things are and, if you have them, technical indicators that might help others identify similar attacks. Your one-month report is the comprehensive post-mortem - what happened, why it happened, and what you did about it.
For incidents that drag on, you'll need a progress report at the one-month mark and a final wrap-up once it's resolved. It's a bit like medical updates during a long treatment - regular check-ins until the patient gets a clean bill of health.
Don't forget to think through how you'll determine when an incident has cross-border impact requiring notifications to multiple authorities. And remember your obligations to let your customers or service recipients know when an incident might affect them - nobody likes finding out about problems from the evening news rather than directly from you.
When an incident hits, you won't have time to start researching who to contact. It's like having your doctor's number ready before you get sick - do the homework ahead of time. Identify the national Computer Security Incident Response Teams (CSIRTs) in every Member State where you operate and keep their contact information at your fingertips.
Build relationships with the single points of contact (SPOC) in each Member State before disaster strikes. It's always easier to call someone you've already met for help rather than introducing yourself during a crisis. For cross-border incidents, you'll need clear guidelines about which authorities to contact when - nobody wants to play phone tag during an emergency.
Get familiar with organizations like the EU-Cyber Crises Liaison Organisation Network (EU-CyCLONe) that coordinate responses to major incidents. Think of them as the cybersecurity equivalent of emergency management agencies during natural disasters - they help coordinate response efforts across borders.
Some industries have sector-specific authorities to report to as well. If that applies to your business, make sure those contacts are part of your emergency directory.
Establish your communication channels with authorities before you need them. Will you report via email, a portal, phone? Who on your team has those details? Make sure more than one person knows the procedures - what happens if your designated reporter is on vacation when an incident occurs?
Help your incident response team understand the broader regulatory ecosystem, including the NIS Cooperation Group that works on consistent implementation across Member States. And don't overlook ENISA (the European Network and Information Security Agency) - they provide valuable guidance that can help you prepare for and respond to incidents more effectively.

Effective vulnerability management begins with a formal Vulnerability Disclosure Policy following international standards like ISO/IEC 29147 and ISO/IEC 30111. This establishes structured processes for receiving and addressing vulnerability reports from third parties like security researchers.
A simple but effective step is implementing a security.txt file at the /.well-known/ location on your websites. This provides clear contact information for security researchers who want to report vulnerabilities they discover.
Your security testing program should include a mix of approaches – regular vulnerability assessments, penetration testing, and red team exercises, each with clearly defined scopes and methodologies. Don't wait until systems are deployed to think about security – embed secure development practices throughout your software development lifecycle, including threat modeling, secure coding standards, and regular security code reviews.
Make security testing a seamless part of your development process by integrating it into CI/CD pipelines with automated security scanning. This allows for early detection of vulnerabilities before code reaches production.
When vulnerabilities are discovered, have clear processes for triaging them based on severity and impact. Define timeframes for remediation based on risk levels to ensure the most critical issues are addressed quickly.
Regular security audits help verify that your implemented controls are actually effective. Establish formal processes for addressing and tracking identified deficiencies until they're resolved.
Consider conducting security architecture reviews during the design phase of new systems and applications. This helps identify security issues before implementation, when they're typically less expensive to fix.
Handle vulnerability information securely, with controlled disclosure processes that balance security needs with appropriate information sharing. Consider joining coordinated vulnerability disclosure programs and engaging with the security research community – these relationships can significantly strengthen your security posture over time.

There's no need to reinvent the wheel for NIS2 compliance. ISO 27001, for instance, provides a comprehensive foundation for establishing an Information Security Management System that covers approximately 70% of NIS2 requirements. You can leverage the Plan-Do-Check-Act cycle from ISO 27001 for continuous security improvement, incorporating regular internal audits and management reviews.
The European Union Agency for Cybersecurity (ENISA) is currently developing EU-wide certification schemes that will eventually become central to demonstrating NIS2 compliance. In fact, under Article 24(3), the European Commission may eventually require Essential Entities to obtain certification under specific European cybersecurity certification schemes.
If you've already implemented industry standards and frameworks like the NIST Cybersecurity Framework or CIS Controls, you can map these to NIS2 requirements to leverage your prior compliance work. This mapping exercise can save significant time and resources.
Consider supporting your NIS2 implementation with governance, risk, and compliance (GRC) platforms. These tools can help centralize policy management, control monitoring, and compliance reporting, giving you better visibility across your organization.
Automated compliance monitoring using security information and event management (SIEM) systems and continuous control monitoring tools provides real-time visibility into your security posture. Similarly, security orchestration, automation and response (SOAR) platforms can streamline incident detection, analysis, and reporting to meet NIS2's strict reporting timeframes.
Using recognized frameworks helps demonstrate due diligence to regulators and can simplify compliance verification during audits and regulatory assessments. Stay informed by monitoring developments in the European cybersecurity certification framework and national certification schemes to anticipate future requirements that might affect your organization.

While compliance is necessary, building a strong security culture creates lasting protection for your organization. Start by establishing cybersecurity as a core organizational value, with clear messaging from executives and visible commitment from leadership at all levels.
Consider developing security champions programs to promote awareness across departments. These representatives, embedded throughout your organization, help translate security requirements into language that makes sense for different business functions.
Work to create a blame-free environment for reporting security concerns and incidents. When people feel safe reporting issues without fear of punishment, you'll discover and address more problems before they become serious incidents.
Rather than treating security as a separate function, integrate cybersecurity into organizational decision-making processes from strategic planning to day-to-day operations. This approach helps security support business objectives rather than appear to hinder them.
To measure progress, implement a defined security maturity model with regular assessments and improvement plans. Your performance metrics should track both security effectiveness and business impact, measuring progress toward risk reduction goals over time.
Reinforce security awareness through multiple channels – training, simulations, internal communications, and recognition programs that celebrate good security practices. Take a risk-based approach to security investments, focusing resources on protecting your most critical assets and processes.
Most importantly, position security as an enabler of digital transformation and innovation rather than an obstacle. When done right, good security supports business growth while managing risks appropriately. Make security decisions collaboratively, involving both security teams and business stakeholders to ensure protective measures are both effective and practical in your specific business context.

The NIS2 implementation requirements are now in effect, and the consequences of non-compliance are severe - up to €10 million in fines, operational restrictions, and potential management bans.
Don't tackle this complex cybersecurity challenge alone.
At Gauss, we specialize in developing custom IT solutions that make NIS2 compliance straightforward and manageable. Our cybersecurity experts can help you:
Conduct a comprehensive gap analysis to identify your specific compliance needs
Implement the 10 mandatory cybersecurity measures required by NIS2
Develop robust incident response protocols to meet strict reporting timelines
Secure your supply chain with effective vendor management strategies
Build a sustainable cybersecurity framework that protects your organization
Let's turn NIS2 compliance from a regulatory burden into a competitive advantage for your business.